Continuous Threat Exposure Management (CTEM): A Proactive Cybersecurity Framework
The Modern Alternative to Vulnerability Management
What Is Continuous Threat Exposure Management (CTEM)?
Continuous Threat Exposure Management (CTEM) is a term first introduced by Gartner® in 2022. CTEM is not a product, but a set of cybersecurity processes and capabilities, laid out across 5 phases, that equip enterprises to continually and consistently evaluate the accessibility, exposure, and exploitability of an enterprise’s digital and physical assets.
How the CTEM Framework Works:
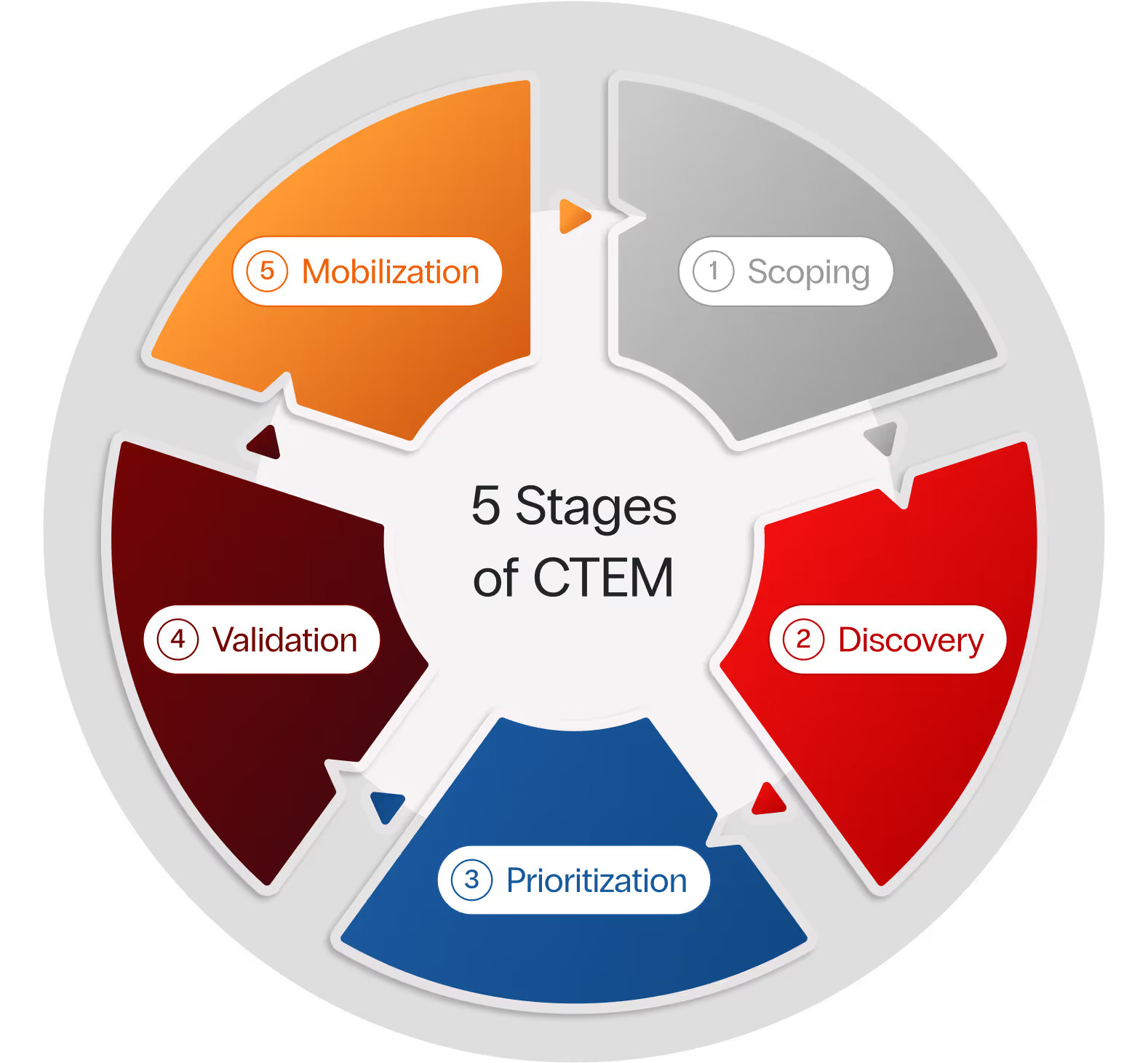
The 5 Stages of a CTEM Program
CTEM is a systematic approach to continuously refine exposure management priorities, operating through a cycle of five key stages. This recurring CTEM lifecycle enables security teams to stay in tune with the evolving threat landscape and eliminate exposures before they become a security incident.
The first phase is that of defining which assets and attack surfaces are in scope for the CTEM program. User endpoints, cloud workloads, data center, to name a few. Security teams should be guided by the priorities of their business stakeholders.
Zafran automatically aggregates, normalizes and de-duplicates vulnerability and asset data from the scanners and security tools you already run—cloud, on-prem and application—so CTEM teams start the scoping phase with one authoritative inventory rather than piecemeal lists.
Use security tools to discover assets, vulnerabilities, and misconfigurations relevant to the CTEM program’s defined scope. Challenge the status quo and seek the ability to continuously detect such exposures. The next phase, Prioritization, will address any concerns of drowning in detections.
When in doubt, remember: the objective of exposure management is to identify and address the threats most likely to be exploited. To avoid being overrun by detections and to move beyond generic severity measures, automate analysis of contextual factors, including threat intel, compensating security controls (aka, defenses), available mitigations, and business criticality, to reveal your biggest risks.
Within the context of CTEM, validation not only includes assessing how the attacker can exploit the exposure, but also verifying the speed, adequacy, and feasibility of the suggested treatment.
To mobilize a group of resources is to organize and coordinate them for maximum effect, which, in this case, is winning the cybersecurity battle. Consider available options. Communicate with and align security and IT teams, rallying them around an achievable risk reduction objective. In this phase, risk reduction may take the traditional form of remediation of root cause (e.g., patching a host OS, updating a cloud workload image), as well as the newer risk mitigation techniques using your existing security tools.
The Business Value of CTEM:
“Why Do I Care?”
Vulnerability exploitations are now the leading initial access vector behind security breaches. Additionally, research proves that CVSS Mediums are exploited more frequently than CVSS Criticals and Highs combined. Sophisticated threat actors are shifting tactics, even as traditional vulnerability management processes leave organizations chasing SLA compliance instead of tackling risk. Our processes and KPIs are not driving the intended behavior, even if we know, intuitively, what better should look like. This is why CTEM matters.
A CTEM program reveals the vulnerabilities most likely to be exploited in your environment. It analyzes factors unique to your organization’s hybrid cloud context, to move beyond generic risk measures and definitively direct limited resources to your biggest threats. One size does not fit all.
A CTEM program mobilizes resources efficiently to create better cybersecurity outcomes. Better coordination, shorter exposure windows, and faster MTTR (Mean Time to Remediate).

CTEM vs. Traditional Vulnerability Management:
What's the Difference?
Traditional vulnerability management (VM) revolves around periodic vulnerability scans, driving the organization to chase SLA compliance tied to generic severity measures (i.e., CVSS). In contrast, CTEM provides a real-time, continuous process to detect, hunt, and proactively eliminate high-risk exposures that attackers are most likely to exploit. It contemplates the factors unique to the organization’s IT environment that necessarily affect risk. In this way, the CTEM-driven VM practice surfaces the most pressing vulnerabilities facing the organization, and more effectively mobilizes resources (people, process, technology) to neutralize the threat.
Benefits of CTEM
for Enterprise Cybersecurity
CTEM delivers measurable value by focusing on exposures that matter most.
Key Benefits Include:
Reduced Risk of Breach: Eliminate initial attack vectors (IAVs) before they can be exploited
Smarter Resource Allocation: Focus security efforts where they’ll have the greatest impact.
Faster Detection and Response: Improve visibility and reaction time to real-world threats.
Alignment with Business Priorities: Ensure cybersecurity decisions support operational goals.
Why Choose Zafran To Support Your CTEM Program?
The Zafran Threat Exposure Management Platform supports the entire CTEM lifecycle, from scoping to mobilization, through a combination of contextualized risk analysis, real-time validation of mitigation techniques, and optimized remediation workflows, all integrated with the customer’s existing security ecosystem
Experience the Zafran CTEM Solution
Join the security leaders who have successfully evolved from reactive Vulnerability Management to proactive Threat Exposure Management. See the difference data-driven prioritization makes with Zafran CTEM Platform.
