Mitigate incidents coming for this hosting service🪆 CVSS 10 Erlang/OTP flaw (SSH protocol messages) wildfire 🔥Flip: Vuln exploitation wins over phishing and identity as the main cause for ransomware

Proton66 campaign targets multiple vulnerabilities
Since January 8th, a campaign initiated from Proton66 is targeting global organizations. Proton66 is a Russian bulletproof hosting service linked to cybercriminal fora and connected to Prospero, another infamous bulletproof service. Two net blocks identified with Proton66 were spotted as actively attempting to deploy different malware strains, access network devices via brute force and scanning various vulnerabilities – such as flaws in Palo Alto (CVE-2025-0108), Mitel MiCollab (CVE-2024-41713), D-Link NAS (CVE-2024-10914) and Fortinet (CVE-2024-55591, CVE-2025-24472). The Fortinet vulnerabilities have been recently exploited by SuperBlack, a new ransomware gang which is apparently a former subsidiary of the now defunct LockBit group.

[mitigate]Block access from the IP ranges 45.135.232[.]0/24 and 45.140.17[.]0/24.[/mitigate]
A Chinese ransomware uses RMM flaws
The Chinese Storm-1175 (aka UNC5604) has been recently exploiting vulnerabilities in the Remote Monitoring and Management (RMM) tool SimpleHelp (CVE-2024-57726/7/8) to deploy a version of the Medusa ransomware. The financially motivated actor is known for targeting VMware ESXi hypervisors and for deploying different ransomwares such as Medusa, Akira and Black Basta.
[mitigate]Block access from 213.173.45[.]230, 194.76.227[.]171, 45.9.148[.]136, 45.9.149[.]112.[/mitigate]
A new campaign targets a NTLM vulnerability
A week after it has been patched, threat actors started active exploitation of a Windows NTLM disclosure vulnerability (CVE-2025-24054) against organizations in Poland and Romania. The flaw is triggered through an archive file sent via a phishing email. Together with it, were found other files which are apparently related to the exploitation of another recent NTLM vulnerability (CVE-2024-43451) and to the infrastructure of the Russian state actor APT28.

Kimsuky leverages a 2019 Microsoft RDP flaw
The North Korean actor Kimsuky (aka APT43) is exploiting “BlueKeep”, an old RCE Microsoft RDP vulnerability (CVE-2019-0708), to get initial access to organizations in the software, energy and financial sectors. The same campaign has also been observed using an old Equation Editor flaw (CVE-2017-11882) triggered via malicious files embedded in phishing emails.
Enable the RDS Network Level Authentication (NLA); Apply FortiGuard IPS signature “MS.Windows.RDP.CVE-2019-0708.Remote.Code.Execution” and Trend Micro Rule 1009749
Sophisticated exploitations of Apple vulnerabilities
Two Apple vulnerabilities are currently exploited in “extremely sophisticated” attacks. The flaws are a memory corruption flaw in CoreAudio (CVE-2025-31200) leading to code execution on a compromised device; and a vulnerability in the hardware block RPAC (CVE-2025-31201) resulting in the bypass of pointer authentication.
Erlang/OTP flaw raises significant concerns
Deep concerns were raised after the disclosure of a critical vulnerability in Erlang/OTP (CVE-2025-32433), with a maximal CVSS score of 10/10. The flaw is the result of an improper handling of SSH protocol messages, allowing unauthenticated attackers to successfully connect. Several POCs have already been made publicly available. Erlang/OTP is a collection of libraries used in real-time distributed systems that require high availability and it is particularly common among critical infrastructures, telecom systems, e-commerce, banking and communication applications such as Whatsapp.
DBIR: rise in vulnerability exploitation, especially in edge devices
A new “Data Breach Investigations Report”, analyzing over 22K real-life incidents, shows that vulnerabilities were exploited in 20% of all breaches (a 34% rise from 2023) and in 20% of ransomwares’ initial access vectors (a number that doubled since 2022). After collecting data from 10K companies which remediated KEV-listed vulnerabilities in 2024, it also reveals that only 38% of CISA KEV vulnerabilities have been fully remediated and that the median time-to-remediate reaches no less than 38 days. While remediation cycles for edge vulnerabilities were slightly faster, attackers were also far quicker to exploit them (in most of most cases they were leveraged as zero-days). In general, edge devices share 22% of vulnerability exploitations – an eightfold increase from 2023. Besides that, the report presents a surge in espionage-motivated attacks, in which vulnerabilities were exploited in 70% of the cases. Finally, it makes clear that GenAI “has still not taken over the world” even though the use of AI model for malicious email generation has increased.
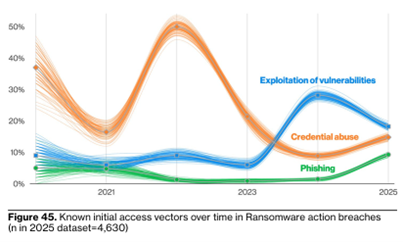
Attackers are growingly attempting to exploit vulnerabilities in post-compromise
Another report reveals that, based upon the analysis of 150 billion monitored security events for 2024, 30% of the attacks implied vulnerability exploitation in public-facing applications. In 25% of the incidents, attackers also scanned for vulnerabilities in post-compromise stage. Besides that, manufacturing remains the most targeted sector (four years in a row), representing 26% of the incidents and closely followed by the finance & insurance industry (23%).
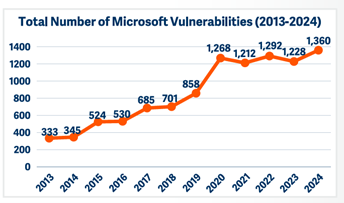
Record high number of Microsoft vulnerabilities
A research shows that a record-high number of 1,360 Microsoft vulnerabilities were disclosed in 2024 – an 11% increase from 2023. Moreover, the number of security bypass flaws surged from 56 to 90. On the other hand, the amount of Microsoft critical vulnerabilities continued its downside trend to only 78 in 2024. Privilege Elevation vulnerabilities was the largest category (40% of total flaws), followed by Remote Code Execution vulnerabilities (32%).
Heading 1
Heading 2
Heading 3
Heading 4
Heading 5
Heading 6
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.
Block quote
Ordered list
- Item 1
- Item 2
- Item 3
Unordered list
- Item A
- Item B
- Item C
Bold text
Emphasis
Superscript
Subscript
Mitigate
Heading 1
Heading 3
Heading 2
Heading 4
Heading 5
Heading 6
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.
Block quote
Ordered list
- Item 1
- Item 2
- Item 3
Unordered list
- Item A
- Item B
- Item C
Bold text
Emphasis
Superscript
Subscript
