2K FWs compromised 🔥 Pivot to vuln exploitation ↩️ Telco companies attacked again through vulnerabilities 📡 Tor+Firefox users attacked through zero-days

Lunar Peek has already compromised 2K firewalls
The Lunar Peek campaign has compromised around 2K Palo Alto firewalls so far, mostly in the US and India. The attack targets a newly discovered PAN-OS zero-day (CVE-2024-0012), chained with another privilege escalation vulnerability (CVE-2024-9474). Since the disclosure of the flaw on November 15, the number of Internet-exposed vulnerable devices worldwide has dropped from 11K to 2.7K, indicating that many organizations have applied a patch, or alternatively disconnected their devices’ Internet connection.

[mitigate]Under Palo Alto’s Threat Prevention subscription, make sure the relevant Threat IDs (95746/7, 95752/3, 95759 and 95763) are in block mode.[/mitigate]
Palo Alto again
In parallel, a vulnerability in Palo Alto GlobalProtect App (CVE-2024-5921) has been disclosed. The flaw, resulting from a certificate validation issue, allows attackers to install malicious root certificates, then gaining the ability to deploy malware. While a patch has been released for Windows versions, Linux and macOS systems remain so far unfixed.
[mitigate]Re-install GlobalProtect with the pre-deployment key FULLCHAINCERTVERIFY set to “Yes”; use GlobalProtect app in FIPS-CC mode. [/mitigate]
BianLian's pivot to vulnerability exploitation
As part of its pivot towards vulnerability exploitation, BianLian is now leveraging Proxyshell vulnerabilities (CVE-2021-34473,CVE-2021-34523, CVE-2021-31207) in both Windows and ESXi servers for initial access. In the past, the group was gaining access though compromised RDP credentials, phishing or initial access brokers. Moreover, BianLian has also been observed exploiting a Windows flaw (CVE-2022-37969) for privilege escalation. Formerly known for its double extortion tactics, the group has now abandoned encryption and is solely focusing on data exfiltration. BianLian is a prominent Russian group which emerged in 2022 and is famous for having targetedAmerican, Canadian and Australian critical infrastructure, as well as healthcare and professional service organizations.

Detect for “Win32.Exploit.CVE-2022-37969” with Zscaler ZIA and ZPA Detection ID 126229
A third party ransomware attack causes large disruptions
A ransomware attack against Blue Yonder, a company providing an end-to-end supply chain platform, is currently disrupting operations of different large customers – including Starbucks, Ford, Procter and Gamble and Sainsbury. The unidentified threat actor allegedly compromised Blue Yonder’s managed services’ environment. The incident has yet to be fully remediated.

Telco companies compromised through vulnerabilities
Salt Typhoon (aka UNC2286) is conducting a new campaign against the Southeast Asian telecommunication sector through a previously unknown malware and the exploitation of various one-day vulnerabilities for initial access. These include the ProxyLogon ones (CVE-2021-26855/57/58, CVE-2021-27065) and flaws in Fortinet EMS (CVE-2024-48788), Sophos Firewalls (CVE-2022-3236) and Ivanti Connect Secure VPN (CVE-2023-46805, CVE-2024-21887). Rather than directly exploiting vulnerabilities within its targets’ environments, the group prefers to first infiltrate third parties (mostly consulting firms and NGO). The Chinese state actor gained recently in notoriety after compromising American large telecommunication firms including Verizon, AT&T, Lumen and T-Mobile.
A Russian state actor, Rejetto flaws and cyberespionage
TAG-110, a Russian group apparently affiliated to the state actor APT28, has targeted organizations in Europe and Asia with a Python backdoor used for data exfiltration and cyberespionage. Except phishing emails, initial access was reached thought the exploitation of vulnerabilities in Rejetto HTTP File Servers, a well-known web-based file server application.
A Chinese state actor, Array flaws and cyberespionage
A Chinese state actor named Earth Kasha (aka MirrorFace), affiliated to APT10, has been exploiting a RCE flaw in Array AG and vxAG secure access gateways (CVE-2023-28461). The attacks targeted vulnerable SL-VPN and file storage services in IT and government organizations in Asia. The flaw was exploited together with a vulnerability in FortiOS (CVE-2023-27997) and in the file sharing system Proself (CVE-2023-45727).

[mitigate]In Array AG/vxAG, blacklist URL requests with the keywords “client_sec” and “%00”[/mitigate]
Firefox and Tor users exposed
Malicious files found on a server used by RomCom (aka UNC2596) showed that, last October, the group chained together a Mozilla zero-day (CVE-2024-9680) with a Windows one (CVE-2024-49039) against American and European targets. As a result, during a short period of time, any user visiting a RomCom-controlled website on Firefox or Tor was infected with a backdoor, as no user interaction was needed. The two vulnerabilities were patched quickly after the disclosure. For the operation, RomCom created fake websites mimicking ones of companies providing IT services, mostly to the government sector. RomCom is a notorious Russian cybercrime, recently shifting to cyberespionage and geopolitically motivated attacks against Ukraine and the US.

Mass exploitation of a ProjectSend vulnerability
Concerns were raised about the possible widespread exploitation of a vulnerability in ProjectSend servers (CVE-2024-11680), a file sharing open-source application. The flaw allows attackers to create malicious accounts, upload webshells or potentially embed malicious JavaScript code. While it was discovered and patched in early 2023, it has been assigned with a CVE ID only last week, after the first reports about in-the-wild exploitation. It is assessed that most of the 4,000 Internet-facing instances found worldwide have not been patched against the flaw.
An individual hacker exploits IoT flaws for DDoS
A threat actor nicknamed Matrix is responsible for a wide DDoS campaign exploiting IoT vulnerabilities to hijack devices into a botnet. Among others, diverse command injections flaws in routers (CVE-2017-18368,CVE-2021-20090) were used. Matrix is allegedly a Russian lone wolf actor.
When a WinRAR flaw is exploited with phishing
A South Asian threat group named Mysterious Elephant (aka APT-K-47) has been using a WinRAR vulnerability (CVE-2023-38831) to target Pakistani organizations. The flaw, exploited to deploy advanced malware, was triggered through a file sent in a phishing email about the Haj pilgrimage.

Flaws in needrestart
Qualys researchers found five Local Privilege Escalation vulnerabilities (CVE-2024-48990/1/2, CVE-2024-10224,CVE-2024-11003) in needrestart - a component installed by default on Ubuntu servers and which scans systems to decide if a restart is needed. The flaws are considered easily exploitable.
[mitigate]Disable the “interpreter heuristic” in needrestart’s config; Detect with Qualys QID 382375[/mitigate]
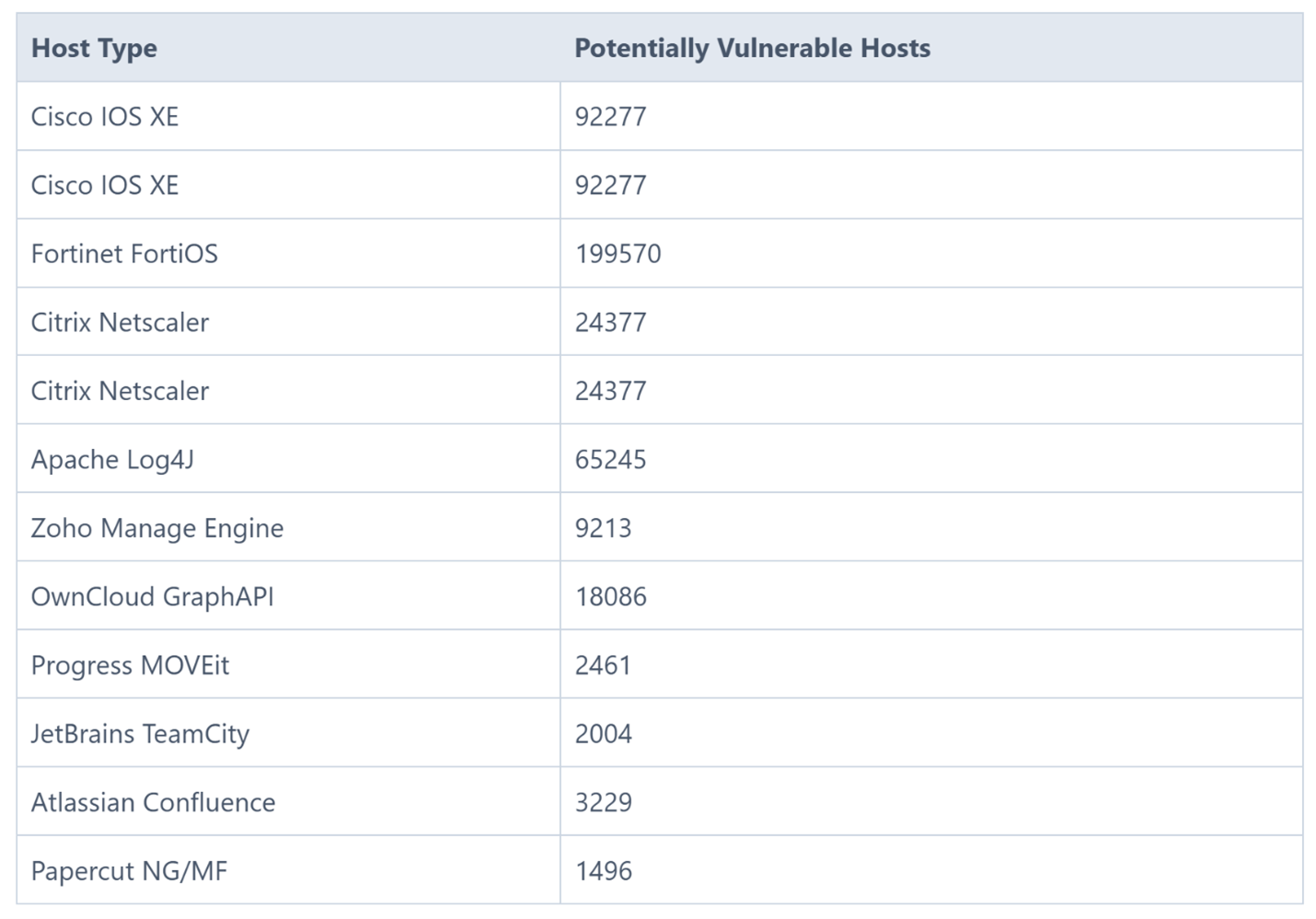
Tens of thousands hosts exposed to most exploited vulnerabilities
A new report found tens of thousands of Internet-exposed hosts vulnerable to the 15 most exploited vulnerabilities for 2023 recently published by CISA. Moreover, more than 60 threat actors were identified targeting the 15 flaws, and 13 vulnerabilities were related to 8 or more known POC exploits.
Heading 1
Heading 2
Heading 3
Heading 4
Heading 5
Heading 6
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.
Block quote
Ordered list
- Item 1
- Item 2
- Item 3
Unordered list
- Item A
- Item B
- Item C
Bold text
Emphasis
Superscript
Subscript
Mitigate
Heading 1
Heading 3
Heading 2
Heading 4
Heading 5
Heading 6
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.
Block quote
Ordered list
- Item 1
- Item 2
- Item 3
Unordered list
- Item A
- Item B
- Item C
Bold text
Emphasis
Superscript
Subscript