Cisco's Firewall under attack - Exploitations undetected for years - GPT-4 generate exploits for 1-day vulnerabilities

A zero-day in the enterprise software CrushFTP (CVE-2024-4040), letting unauthenticated attackers escape the Virtual File System and download system files, is apparently exploited in the wild against various US entities. The flaw, which exploitation is considered trivial, affects versions below 11.1 and allegedly can’t be exploited if the CrushFTP instance operates under a DMZ.
[mitigate]Use Crowdstrike Falcon Insight XDR specific query [1] ; install Rapid7 Insight Agent on all applicable hosts and run the detection “Suspicious Web Request - Possible CrushFTP (CVE-2024-4040) Exploitation”. [/mitigate]
The MITRE corporation admitted that in early January, a state actor breached one of its research and prototyping networks. The attacker leveraged two of the Ivanti Connect Secure’s zero-days (CVE-2023-46805, CVE-2024-21887) to compromise a VPN admin account, then moved laterally to MITRE’s VMWare infrastructure. Among others, the vulnerability has been exploited by the Chinese APT UNC5221, possibly affiliated to Volt Typhoon.
The GRU-afiliated cyberespionage group APT28 (aka Forest Blizzard) has used a post-compromise custom tool nicknamed GooseEgg in order to exploit a vulnerability in the Windows Print Spooler service (CVE-2022-38028). GooseEgg apparently served the purpose of stealing credentials and escalating privileges against targets in Ukraine, Europe and North America. The vulnerability, first exploited in 2020, was disclosed only two years later.

[mitigate]Activate Tenable Plugins 166025, 166028-30, 166032, 166034, 166036, 166039.[/mitigate]
STORM-1849 (aka UAT4356) has been exploiting two vulnerabilities in Cisco’s FirePower Threat Defense devices and ASA firewalls (CVE-2024-20353, CVE-2024-20359) since November 2023, apparently targeting governments worldwide. The group is a new cyberespionage actor possibly from China, which proved a deep knowledge of the targeted devices. The flaws have been leveraged to deploy a backdoor allowing the attackers to perform operations such as configuration modification, reconnaissance, network traffic capture/exfiltration and lateral movement. The group’s initial access vector remains unknown.

Check Qualys ID 317450 and 317451.
The North Korean infamous Kimsuky group has exploited vulnerabilities in the update mechanism of the eScan antivirus to deploy a new cryptomining backdoor named GuptiMiner. Kimsuky leveraged the fact that eScan downloads were not signed and didn’t used HTTPS. The issue existed for five years before being patched in 2023.
Concerns have been raised since the publication of a PoC for a vulnerability in Progress Flowmon (CVE-2024-2389) – a network monitoring tool used by more than 1500 companies including Sega, Kia, Volkswagen or Orange. The PoC was released with a demo showing how to plant a webshell and to elevate privileges to root.
CISA issued a warning about Akira, a notorious triple extortion group which since March 2023 has impacted more than 250 organizations and earned 42 million USD. According to CISA, the group, that pivoted to target Linux servers, mostly reaches initial access by leveraging known Cisco’s vulnerabilities (CVE-2020-3259, CVE-2023-20269).
Microsoft suspended a patch for an Outlook information disclosure vulnerability (CVE-2023-35636), allowing attackers to steal NTLM hashes via maliciously crafted files. Issues have been found within the patch, that was released in early April. In the meantime, before releasing a new patch, Microsoft offers mitigation recommendations.

[mitigate]Add a new DWORD key with a value of '1' to two different keys, in the Group Policy registry path and the OCT registry path.[/mitigate]
An academic study proved that GPT-4 is now able to autonomously exploit one-day vulnerabilities. The experiment provided descriptions of 15 one-day vulnerabilities to the LLM, which successfully exploited 87% of them. In comparison, other LLMs (such as GPT-3.5) failed to generate any exploit.
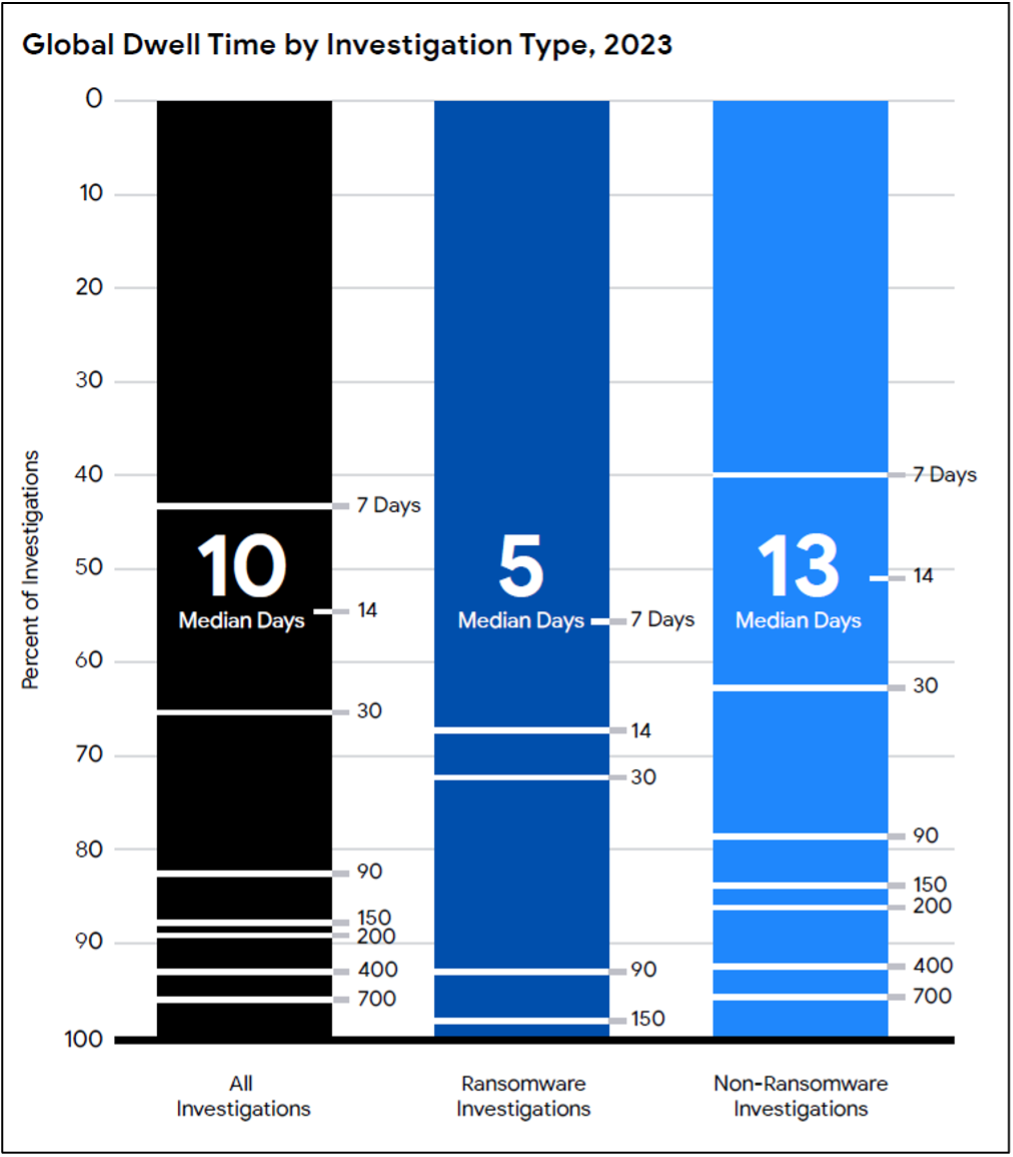
A new comprehensive report about 2023 trends shows that vulnerability exploitation remains the preferred initial access method and has been used in 38% of the attacks. Moreover, it confirms a particular focus of espionage actors in zero-days within edge devices, uncovered by EDRs. The report also reveals that the median “dwell time’, i.e. the numbers of days an attacker is present but undetected, has been reduced from 16 to 10.
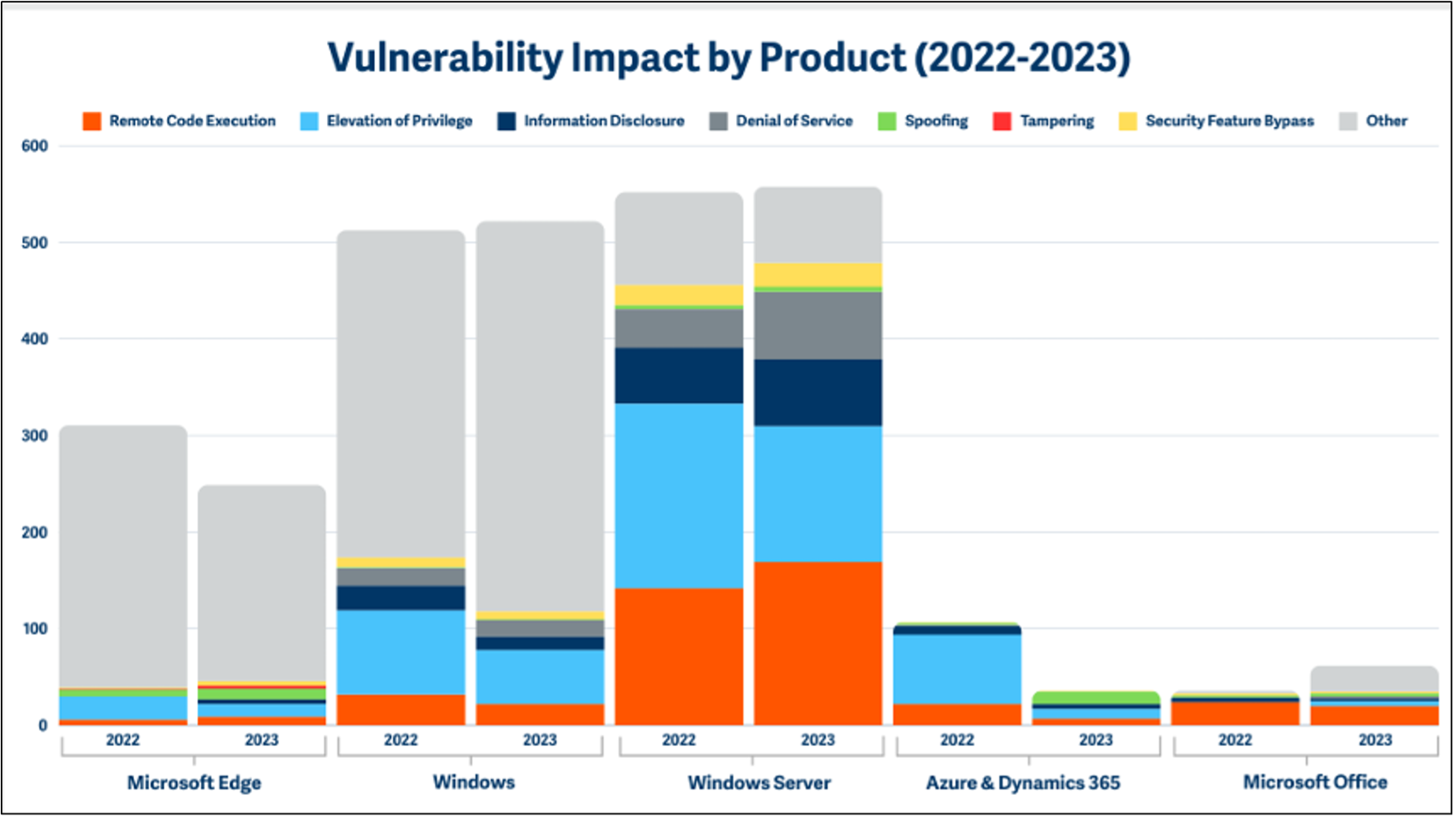
A new report shows that the downward trend in the number of Microsoft’s critical vulnerabilities continued in 2023. However, while privilege escalation flaws decreased from 2022, the number of Microsoft’s RCE vulnerabilities rose by 13% to reach 356 – party due to a pick in Windows servers’ vulnerabilities. It has also been found that Denial-of-Service vulnerabilities climbed by 51% from 2022.
Heading 1
Heading 2
Heading 3
Heading 4
Heading 5
Heading 6
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.
Block quote
Ordered list
- Item 1
- Item 2
- Item 3
Unordered list
- Item A
- Item B
- Item C
Bold text
Emphasis
Superscript
Subscript
Mitigate
Heading 1
Heading 3
Heading 2
Heading 4
Heading 5
Heading 6
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.
Block quote
Ordered list
- Item 1
- Item 2
- Item 3
Unordered list
- Item A
- Item B
- Item C
Bold text
Emphasis
Superscript
Subscript