Aligning Zafran to the Gartner® CTEM Framework
Why CTEM, Why Now?
Vulnerability exploitation is now the leading initial access vector behind security breaches. Traditional VM programs leave security teams drowning in alerts. All too often, they lack the context that shows which exposure presents the biggest risk, instead overrotating on generic measures of severity. Continuous Threat Exposure Management (CTEM) changes all that.
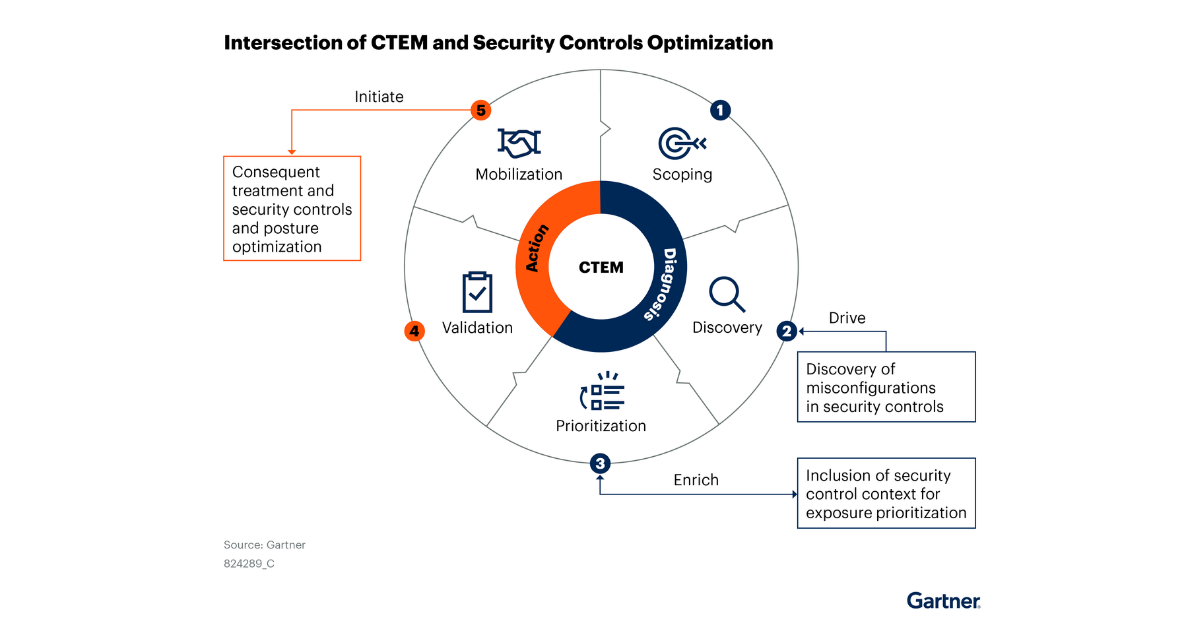
A term first coined by Gartner in 2022, CTEM is a set of cybersecurity processes and capabilities that replaces that “patch-everything” treadmill. Laid out across five phases (ie, Scoping, Discovery, Prioritization, Validation and Mobilization), CTEM enables security teams to continuously evaluate, prioritize, and resolve the organization’s biggest exposures. CTEM reveals the vulnerabilities most likely to be exploited in your environment. This is why CTEM matters.
Exposure Window The average time to exploit is 5 days; the average time to patch is 49.
Through a continuous loop of detection, prioritization, and response, CTEM programs shrink the exposure window, not by chasing every CVE, but by focusing teams on the exploits that matter most. Zafran’s Threat Exposure Management Platform was built around that exact cycle, from its unified inventory to its RemOps engine for closing the loop.
CTEM at a Glance
The CTEM process operates across five interconnected phases – Scoping, Discovery, Prioritization, Validation, Mobilization. Zafran supports the entire CTEM lifecycle through a combination of contextualized risk analysis, real-time validation of mitigations, and automated remediation workflows, all integrated with the customer’s existing security ecosystem. Let’s explore each phase one by one.
Scoping
In the first phase, the organization defines which assets and attack surfaces are in scope for their CTEM initiative. Examples may include user endpoints, cloud workloads, and data centers tied to a specific department or business service.
Zafran helps align CTEM efforts with business objectives by building a contextualized exposure map that reflects organizational risk. Through integration with CMDBs, asset inventories, and vulnerability scanners, Zafran helps teams identify which environments, systems, and business-critical applications pose the greatest risk if exploited. This enables organizations to scope their CTEM program around truly exploitable risk—not just based on asset volume or CVSS scores.
TIP When kicking off your CTEM program, start small. Nothing breeds success like success, so defining a limited scope enables you to refine your process as you apply learnings. As you build momentum and your initiative’s muscle memory, you can expand the scope of your CTEM journey.
Discovery
In the Discovery phase, security teams use various tools to discover assets, vulnerabilities, and misconfigurations within the CTEM program’s defined scope. Zafran supports Discovery in a few ways.
First, the Zafran Threat Exposure Management Platform aggregates and normalizes vulnerability, asset, and control data from multiple sources—cloud, on-prem, and third-party tools—into a unified view. It supports discovery of known and unknown exposures through integrations with scanners (Tenable, Qualys, Wiz), EDR tools, CMDBs (ServiceNow, Jira), and network mapping. Zafran also has its own continuous vulnerability detection capability which operates agentlessly.
Zafran identifies if vulnerabilities are present during runtime and whether affected assets are exposed to the internet, providing deeper risk context than static vulnerability lists based on CVSS. Zafran also enables proactive threat hunting, to identify vulnerabilities known to be targeted by specific threat actors.
Prioritization
The objective of exposure management is to identify and solve the threats most likely to be exploited. Going far beyond generic severity, Zafran automates analysis of contextual factors like internet exposure, runtime presence, compensating security controls, threat intel, and more, to pinpoint and automatically prioritize your biggest risks. It uniquely accounts for the presence and effectiveness of deployed controls (e.g., firewalls, EDRs, WAFs), revealing which vulnerabilities are realistically exploitable in the current environment. The platform uses runtime telemetry, control policy inspection, and exposure graphs to prioritize the top 10% of vulnerabilities most likely to be exploited, cutting false positives by 90%.
“Zafran has reduced the number of urgent critical vulnerabilities by accurately highlighting those that need immediate attention. As a result, it strengthens our security posture by ensuring that we allocate resources effectively, minimize risk exposure, and maintain continuous protection against evolving threats.”
- Senior Security Analyst, Healthcare Company with 10k+ Employees
Validation
Validation not only includes assessing how the attack can exploit the exposure, but also verifying the speed and feasibility of the suggested treatment. Zafran validates exposure and control gaps by mapping observed vulnerabilities and exposures to attacker techniques (MITRE ATT&CK) and compensating controls. Instead of performing synthetic attacks, Zafran analyzes security policies and deployed defenses (e.g., WAF rules, EDR blocklists) to determine if they effectively mitigate specific attacker techniques. This results in real-time validation of security posture without disrupting production.
Mobilization
With the most vital exposures prioritized and validated, now is the time to act on this information. Zafran mobilizes response action through its RemOps engine, which uses generative AI to translate prioritized vulnerabilities into consolidated, high-fidelity remediation tasks. It automatically routes tickets to the right owners (e.g., IT, DevOps) through Jira or ServiceNow, reducing ticket noise and improving coordination. Zafran also enables pre-patch mitigations via existing controls and tracks remediation progress through reporting and exposure monitoring. This accelerates MTTR and closes the loop from detection to action.
CTEM vs Traditional Vulnerability Management
A traditional VM program operates around periodic vulnerability scanning. Generic risk measures (CVSS) were meant to be a starting point, not the crutch they have more oftened come to represent. So, organizations wind up chasing Critical and High severity vulns, categorized as such by the generic risk measure, and chase SLA compliance tied to severity.
In contrast, CTEM provides a continuous process to detect, hunt, and proactively eliminate what are actually your highest risk exposures. Not by generic severity measures, but through deep contextual analysis of your hybrid cloud footprint. In doing so, CTEM reveals the most pressing vulnerabilities your organization faces, and more effectively mobilizes resources (people, process, and technology) to drive more impactful risk reduction.
Key Outcomes & Metrics
Enterprises and some of the world’s most iconic brands are already achieving outstanding results using Zafran to ignite improvement, transforming their old VM practices into CTEM powerhouses. On average, customers report a 90% reduction in CVSS Criticals.
A senior cybersecurity leader with a large financial services enterprise reports that Zafran has reduced stress from so-called “panic patching” and enabling them to better focus limited resources where they will have the greatest impact.

A Fortune 20 healthcare enterprise had a similar experience in improving risk assessment and prioritization. In fact, they report that Zafran reduced their CVSS Criticals by 94%. Similarly, yet another healthcare enterprise reported an 87% reduction in the number of Priority 1 (P1) vulnerabilities requiring high urgency.

Through automated contextual risk analysis, Zafran customers benefit from improved prioritization. In turn, this greatly suppresses noise into their remediation efforts, which drives focus and outcomes. Some enterprise customers report 3x faster mean time to resolve (MTTR).
Key Benefits
- Pinpoint and focus on your biggest threats, reducing noise
- Rapidly mitigate risk using your existing defenses, without waiting on patching
- Proactively hunt for threat and exposures before they become an incident
- Slash mean time to resolve (MTTR)
Conclusion
CTEM is not a product, but a program consisting of people, process, and technology. Zafran supports every phase of the CTEM lifecycle (scoping, discovery, prioritization, validation, and mobilization) to deliver measurable risk reduction quickly. This in turns helps you transform your legacy vulnerability management practice into a well-oiled machine that is prioritizing, validating, and resolving your biggest exposures.
Ready to move your CTEM initiative forward? Continue exploring the Zafran Threat Exposure Management Platform at zafran.io/platform. Check out use cases and especially customer case studies over on PeerSpot, to hear what customers have to say about Zafran when we are not in the room.
When you are ready, we are happy to speak with you. Just pound that Get a Demo button.
Request a demo today and secure your organization’s digital infrastructure.
