Making the Business Case for Continuous Threat Exposure Management (CTEM)
Cybersecurity has evolved from an IT concern to a board-level business priority. With 50% of corporate boards now ranking cybersecurity threats among their top five business issues, executives are demanding more than periodic security assessments and reactive patch management. They want continuous, measurable risk reduction that aligns with business objectives and regulatory requirements.
Continuous Threat Exposure Management (CTEM) addresses this demand by transforming security from episodic scanning to a strategic, business-aligned risk reduction program. Unlike traditional vulnerability management that produces overwhelming lists of CVEs, CTEM's five-step cycle (scoping, discovery, prioritization, validation, and mobilization) creates an actionable framework that executives can understand and measure.
The stakes are clear: organizations using CTEM are predicted to suffer two-thirds fewer breaches by 2026. In today's threat landscape where attack surfaces expand by 300+ new services monthly and vulnerabilities are weaponized within 24 hours in nearly 30% of cases, building a compelling business case for CTEM isn't just about security; it's about business survival and competitive advantage.

What Is CTEM and Why Now?
CTEM represents a fundamental shift from periodic, reactive security to continuous, proactive exposure management. Defined by Gartner as "a set of processes and capabilities that continually and consistently evaluate the accessibility, exposure and exploitability of an enterprise's digital assets," CTEM is not a single tool but a structured program that addresses the reality of modern cyber risk.
The current threat landscape underscores why this approach is essential. Breach costs have surged to an average of $4.44 million in 2025 in the U.S., while global vulnerability disclosures hit a record 40,000+ CVEs in 2024. More concerning is the velocity: attackers now weaponize new flaws within hours, far outpacing traditional monthly or quarterly patch cycles.

The five phase CTEM cycle provides a framework that executives can grasp:
- Scope: Define critical assets and attack surface boundaries based on business impact
- Discovery: Continuously identify vulnerabilities, misconfigurations, and exposures across all environments
- Prioritization: Focus on threats that combine high exploitability with significant business impact
- Validation: Test and simulate attacks to confirm exploitability and defensive gaps
- Mobilization: Deploy fixes and compensating controls through coordinated remediation efforts
This continuous loop ensures that security efforts align with both threat reality and business priorities, creating measurable outcomes that resonate with leadership.
Key Challenges Driving CTEM Adoption
Modern organizations face a perfect storm of challenges that traditional security approaches cannot address effectively. Understanding these pain points is crucial for building internal support for CTEM initiatives.
Overwhelming Volume and Velocity: With over 23,600 vulnerabilities published in just the first half of 2025, which is 16% more than the previous year, security teams are drowning in alerts. Traditional approaches that attempt to address every finding inevitably fail, leaving critical issues buried in backlogs while teams chase low-impact vulnerabilities.
Expanding Attack Surfaces: Cloud adoption, remote work, and SaaS sprawl have created unprecedented complexity. Organizations add hundreds of new services monthly, each introducing potential exposures that periodic scans miss. The result is a constantly evolving attack surface that static assessment approaches cannot adequately cover.
Context Blindness: Legacy vulnerability management treats every environment identically, ignoring whether exploit code exists, whether systems are internet-facing, or whether compensating controls already provide protection. A critical score CVE on an air-gapped lab server poses minimal risk, while a medium score vulnerability on a domain controller could be catastrophic.
The Exposure Gap: Research shows that 82% of organizations saw the gap between discovered exposures and remediation capability increase in 2023. The average organization still takes 49 days to close vulnerabilities after identification, creating extended windows for exploitation.
Operational Friction: Security teams discover and prioritize vulnerabilities, but IT and DevOps teams handle remediation. Without clear handoffs, enriched tickets, and shared SLAs, even well-prioritized findings stall in queues while critical fixes languish.
These challenges create a reactive security posture where teams perpetually play catchup with adversaries who move faster than patch cycles allow.
Business Value Translation: Speaking ROI and Risk
To secure executive buy-in, security leaders must translate CTEM's technical benefits into business language that resonates with CFOs, boards, and business unit leaders.
Hard Cost Savings represent the most tangible benefits. Avoiding a single major breach can save millions. By continuously addressing exposures, CTEM reduces breach probability and the associated expected losses. For example, if an organization faces a 25% annual chance of a $5 million breach, CTEM might halve that risk, avoiding $625,000 in expected annual losses.
Beyond breach avoidance, CTEM delivers operational savings by reducing labor hours spent on manual tooling and improving threat detection. Organizations report significant efficiency gains: Zafran estimates that this efficiency translates directly into cost savings, with organizations saving from $169K to over $2.7M annually, depending on size and industry.
Soft Benefits around trust and brand protection are equally valuable but harder to quantify. Consumer research shows that 87% of customers expect companies to protect their data, with 38% willing to sever business relationships following security breaches. In B2B contexts, strong cybersecurity becomes a competitive differentiator that can accelerate sales cycles and support premium pricing.
Risk Quantification using frameworks like FAIR (Factor Analysis of Information Risk) provides the analytical rigor that executives expect. FAIR models risk as Annual Loss Expectancy (probability × impact), enabling teams to demonstrate specific risk reduction in dollar terms.
Building the Internal Case: Stakeholder Perspectives
Success requires addressing the specific concerns and motivations of each stakeholder group while establishing baselines that demonstrate improvement.
CISOs and Security Leadership face the challenge of mounting threats with limited bandwidth. They need a way to continuously understand organizational exposure and communicate security status in business terms. CTEM addresses these needs by providing persistent visibility and risk-based prioritization that yields metrics like exposure time and risk trends for board reporting.
CIOs and IT Operations worry about balancing security demands with uptime requirements and project delivery. CTEM is risk-based and surgical and helps IT focus on the most dangerous issues before attackers exploit them, ultimately preventing emergency situations that do cause downtime. By integrating with IT workflows through ITSM ticketing, CTEM improves collaboration rather than creating friction.
CFOs and Finance Teams need a clear return on investment for cybersecurity spending, as well as protection against unpredictable financial losses from cyberattacks. CTEM helps by improving a company's cyber insurance position, which can lead to lower premiums and better coverage. This approach helps demonstrate a significant reduction in loss frequency relative to the program's cost, positioning it as a way to optimize existing security spending, rather than simply adding to it.
Business Unit Leaders want security that enables rather than impedes business objectives. CTEM reduces security friction by preventing urgent firefights that derail product launches or client deliverables. Continuous monitoring enables faster risk-based decisions for new technology adoption while simultaneously protecting the business unit's reputation and sales prospects.
Common Objections and Strategic Responses
Anticipating and addressing stakeholder concerns strengthens the business case and demonstrates thorough planning.
"We already have vulnerability management. Isn't this just rebranding?" CTEM represents an evolution beyond traditional VM's periodic, overwhelming approaches. While VM produces long lists of CVEs that may overwhelm teams, CTEM provides continuous, prioritized, and holistic risk management. It covers areas that basic vulnerability scans miss, such as misconfigured cloud services, leaked credentials, and unsafe defaults, which are often the actual breach vectors. Research shows CTEM organizations are three times less likely to suffer breaches compared to traditional VM approaches.
"This sounds expensive in a tight budget environment" CTEM is optimization rather than pure addition. The investment prevents far larger reactionary costs, such as a $4+ million breach. Additionally, CTEM can reduce other line items such as external pentesting costs and may improve cyber insurance terms. Start small with existing tools used more effectively under the CTEM framework, demonstrating ROI before expanding investment.
"Our team lacks bandwidth and skills for continuous operations" CTEM actually reduces analyst workload by filtering noise and focusing on critical issues. Instead of sifting through thousands of findings, analysts concentrate on the 5-10% that truly matter. Many CTEM functions can be automated or augmented through managed services, and the proactive approach reduces emergency firefighting that burns out teams.
"Won't continuous testing disrupt operations or overwhelm us with data?" Modern CTEM implementations are designed for safety and control. Validation exercises use read-only checks or isolated test environments, and leading organizations across industries implement continuous validation without operational disruption. Rather than increasing data volume, CTEM implements intelligent filtering that reduces noise while providing actionable insights.
Zafran’s Solution
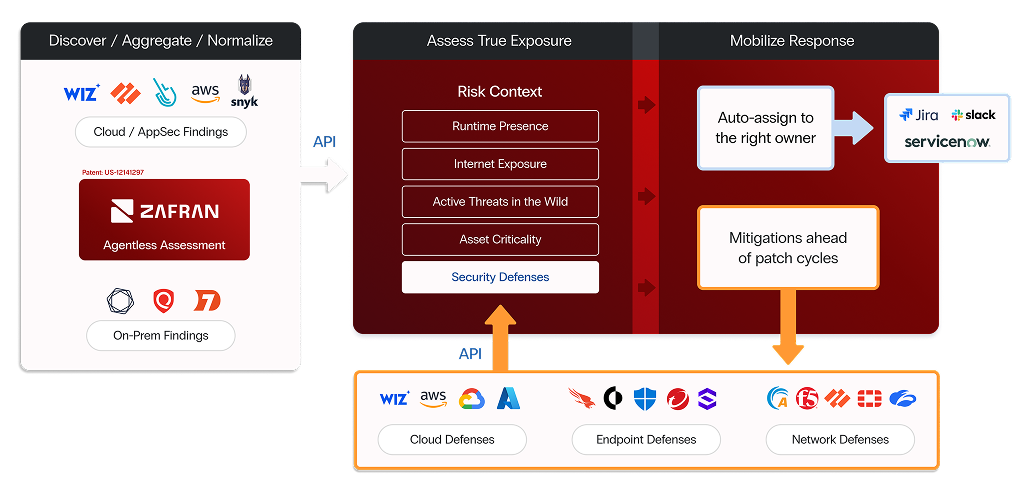
Zafran was designed specifically to tackle these challenges by embedding best practices into a unified, AI-powered threat exposure management platform. Each capability directly addresses the exact pain points that hold organizations back today:
- Filter Noise with Contextual Intelligence. Zafran ingests scanner, cloud, identity, and endpoint signals without requiring new agents, creating a unified picture of exposures across the enterprise. It then layers in runtime evidence, verifying whether the vulnerable component is actually running in memory, as well as internet reachability checks to determine if the asset is externally exposed and therefore more attractive to attackers. On top of this, Zafran validates compensating controls such as WAF rules or firewall policies to confirm whether the vulnerability is already mitigated by existing defenses. By combining runtime presence, internet-facing exposure, and control validation, Zafran proves that up to 90% of “critical” findings are not actually exploitable. This level of precision cuts through the noise and ensures security teams spend their limited time on the exposures that truly matter.
- Mitigate Fast with Compensating Controls. Zafran doesn’t make you wait weeks for a vendor patch. Instead, it tells you exactly which existing defenses, such as WAF, EDR, or firewall access control lists (ACLs), should be updated to block the threat immediately. By neutralizing high-risk exposures within hours, Zafran closes the dangerous “exploit-to-patch” gap and reduces organizational risk in real time.
- RemOps Engine for Smarter Workflows. Zafran’s generative AI deduplicates overlapping CVEs, bundles them into single high-fidelity “golden tickets,” and auto-routes them into Jira or ServiceNow with clear, actionable instructions. This automation eliminates ticket fatigue and guarantees the right fix lands with the right team.
- Executive Dashboards for Business Alignment. Zafran translates complex technical metrics into board-ready insights, such as exposure vs time trendlines and progress against risk appetite. This enables leadership to see measurable risk reduction, not just patch counts, driving informed strategy and investment decisions.
By directly addressing the problems of noise, delays, workflow fatigue, and poor visibility, Zafran transforms CTEM mobilization from an aspirational goal into an operational reality.
Conclusion
Building a compelling business case for CTEM requires translating security outcomes into business value that resonates with diverse stakeholder groups. The current threat environment, which is characterized by rapid exploit weaponization, expanding attack surfaces, and overwhelming vulnerability volumes, makes continuous exposure management not just beneficial but essential for organizational survival.
Success hinges on demonstrating clear ROI through risk quantification, addressing stakeholder concerns proactively, and proving value through focused pilots before enterprise-wide rollout. Organizations that effectively communicate CTEM's benefits gain three strategic advantages:
- sharper focus on truly dangerous exposures,
- faster mitigation that disrupts attack chains, and
- clearer communication across Security, IT, and business stakeholders.
The question isn't whether CTEM provides value. Research consistently shows dramatic risk reduction for adopting organizations. The challenge is building internal consensus and securing investment for what represents a fundamental shift toward proactive, business-aligned cybersecurity. Those who successfully make this case will find themselves better positioned to protect what matters most while enabling business growth in an increasingly digital world.
See Zafran in Action
