Migrating from RBVM to CTEM in a Few Key Steps
Risk-based vulnerability management (RBVM) nudged security teams beyond raw CVSS scores, yet it was only a waypoint on the exposure management journey. Security teams are still drowning in alerts, with little more than threat intel layered atop CVSS to dimly light a path forward. Threat actors are exploiting vulnerabilities and exposures using advanced tactics, automation, and even AI. The average time to exploit now sits at 5 days.
Continuous Threat Exposure Management (CTEM) meets this challenge head-on, prioritizing, validating, and responding to what are actually the organization’s biggest risks. This article discusses how to migrate from RBVM to CTEM in pragmatic, business-aligned steps that every team can follow, to focus finite resources on the most exploitable threats and accrue quick wins.
What Is CTEM?
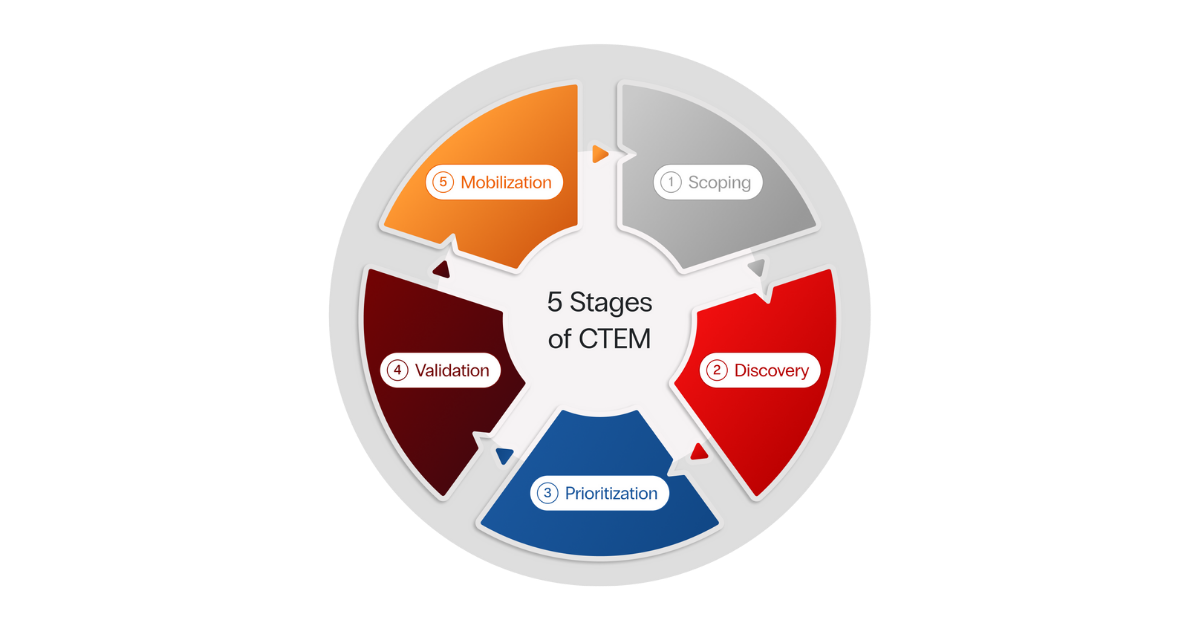
Continuous Threat Exposure Management (CTEM), a term first coined by Gartner in 2022, is a set of cybersecurity processes and capabilities, laid out across a 5-phase framework: Scoping, Discovery, Prioritization, Validation, and Mobilization. CTEM equips enterprises to continuously evaluate the exploitability of their virtual and physical assets, validate their exposure, and rapidly mobilize resources to address them.
- Scoping. Define which assets and attack surfaces are in scope for the program. Start small, to apply learnings which refine efficiency and build momentum.
- Discovery. Automate discovery of assets, vulnerabilities, and misconfigurations relevant to the defined scope. Proactively hunt for exposures.
- Prioritization. Stop drowning in alerts that don’t matter to your unique context. Automate analysis of various factors to reveal the exposures most likely to be exploited.
- Validation. Validate not only how the attacker can exploit the exposure, but also verify the speed, adequacy, and feasibility of the response action.
- Mobilization. Align Security and IT teams around an achievable risk reduction objective, such as remediation of root cause (e.g., patch at host OS image) or mitigation via existing security tools.
Through continuous exposure detection and prioritization using enhanced context (e.g., internet exposure, runtime presence, compensating controls, threat intel), organizations more readily filter out so-called “critical” findings that pose little real-world risk, and focus their resources on the exposures which are most likely to be exploited.
Key Challenges When Advancing Beyond RBVM
Evolving into a CTEM-ready program means confronting several stubborn obstacles that RBVM only partially addressed. Understanding why these issues persist, and how they interact, prevents false starts and sets realistic expectations.
- Shadow Assets and Visibility Gaps
Periodic inventories are practically outdated the moment they are printed. While RBVM may very well have periodic discovery integrated with their CMDB, the speed and scale of today’s threat landscape demands more timely and reliable visibility. Aggregate/unify this data from multiple sources to build a more complete picture. The Practical Guide to Evolving VM to CTEM urges security leaders to treat blind spots as a first-order risk factor rather than a bookkeeping annoyance. Without continuous discovery, every other phase of CTEM rests on an unstable foundation.
- Static Scanning in a Just-in-Time World
Periodic weekly or monthly vulnerability scan cadences were originally designed for static on-prem servers, at a time of “big bang” software delivery cadences. Today, attackers weaponize new CVEs within hours, using automation and even AI which necessitate a more rapid detection capability. Zafran’s maturity model elevates scan frequency from “weekly” in Stage 3 to “at least daily” (plus change-triggered rescans) in Stage 4, aligning detection speed with infrastructure volatility. Anything slower simply cedes initiative to threat actors.
- Low Signal, High Noise, Shallow Context
RBVM improved incrementally on raw CVSS, yet still relies heavily on severity scores plus light threat-intel tags. As such, it still floods security teams with noise. CTEM demands richer context, such as runtime presence, internet reachability, business criticality, and compensating controls, to filter out the 90% of “critical” findings that pose no real danger. Without these factors, “critical” labels proliferate and remediation stalls.
- Fragile Data Quality
Adding new signals too quickly can backfire. The Practical Guide cautions that inaccurate or incomplete enrichment data “could negatively impact your assessment of risk and also cause your stakeholders to lose trust” in the prioritization process. Mature CTEM programs stage context rollouts carefully, validating each feed before it influences scoring.
- Fragmented Ownership
Discovery and prioritization often sit with cybersecurity teams, but patching lives with IT Ops, DevOps, or business unit owners. Without clear hand-off protocols and shared KPIs, urgent vulnerabilities morph into languishing tickets. Zafran highlights this communications gulf as one of the “biggest challenges,” emphasizing the need for clear, timely, and actionable hand-offs.
- Manual Workflows That Don’t Scale
Many RBVM shops still juggle spreadsheets, email threads, and copy-pasted scanner exports. The maturity model pegs these “manual spreadsheets and emails” at Stage 1, long before CTEM’s real-time dashboards and automated routing kick in. Until remediation pipelines are automated, context-rich prioritization simply produces more sophisticated backlog reports that die at the bottleneck.
- SLA Drift and Accountability Gaps
Even when tickets flow, they frequently stall without progressive escalation. Zafran recommends automation that escalates unresolved vulnerabilities to the owner’s manager after a certain time (whatever makes sense for your org) and up the chain as deadlines continue to slip, embedding accountability into the workflow fabric. Such mechanisms transform SLAs from aspirational policy into enforceable practice.
Addressing these seven challenges in concert (ie, visibility, cadence, context, data quality, ownership, workflow automation, and SLA enforcement) creates the operational bedrock on which CTEM can thrive.
Best Practices for a Smooth Migration
A successful journey from RBVM to CTEM advances through five tightly-linked capability areas. Think of each as a flywheel that gains momentum with every improvement you make in the others.
- Build an always-on asset inventory.
Aggregate data from multiple sources regularly, to build a comprehensive and representative inventory. Collaborate cross-functionally between IT and Security to define a standardized data model that reflects all essential asset and device information, including relationships between them. Treat your colleagues in IT Asset Management like the strategic partners that they are: continous asset discovery plays a key role in your CTEM initiative’s success. Automate workflows for newly discovered assets that records ownership and metadata, and formalize regular reviews to validate the quality of asset data.
- Treat every infrastructure change as a potential exposure event.
Weekly authenticated scans are a step forward, but modern environments mutate hourly. Raise the baseline from weekly scan to daily - or even better, change-triggered - that combine agents and agentless methods. Integrate scanners into CI/CD so container images are vetted before deployment, and monitor KPIs such as “percentage of critical assets scanned within SLA” to prove coverage.
- Prioritise with context, not just scores.
RBVM’s mix of CVSS and basic threat intel often floods teams with noise. CTEM filters findings through runtime presence, internet reachability, business importance, and the status of compensating controls, elevating only the genuinely exploitable few exposures which have heretofore hidden within the noise. As you add context factors, validate data quality rigorously; inaccurate inputs erode stakeholder trust.
- Institutionalise hypothesis-driven exposure hunting.
Beyond scanning lies proactive discovery of attack paths attackers will exploit next. Launch short, focused campaigns (e.g., “End-of-life kernels on internet-facing Linux servers”) and document hypotheses, data sources, results, and quick mitigations. Automating the hunt process frees analysts for deeper investigations and keeps the program learning from its own trends.
- Close the last-mile gap with clear ownership and automation.
Even perfect prioritisation fails if tickets die in limbo. Formalise remediation SLAs in security policy, store ownership data in a single source of truth, and push richly annotated tickets (asset, CVE, fix, due date) through the ITSM platform teams already use. As maturity grows, automate ticket routing, add risk-based escalations, and surface exceptions for unowned assets. Escalations that climb the management chain after five days of SLA breach keep momentum high without constant manual policing.
- Handle edge-case assets deliberately.
Operational-technology devices, legacy servers, or systems that cannot host agents still need coverage. Fall back to authenticated scans or deploy compensating controls such as network segmentation and strict firewall rules, and track these exceptions in the same dashboards that monitor mainstream assets.
Seven Tips to Drive Quick Wins
- Progress beats perfection. Double scan cadence incrementally (monthly → bi-weekly → weekly) instead of waiting for a big-bang shift. Don’t fall into the trap of waiting for perfection.
- Measure success. Metrics like mean-time-to-detect (MTTD) and exploitable backlog percentage prove value to executives and sharpen internal focus.
- Escalate automatically. Missed SLAs should rise to the owner’s manager without manual chasing. Use further escalations strategically as a governance mechanism that improves visibility and outcomes.
- Expose orphaned assets weekly. Publishing “assets without owners” reports surfaces data-quality gaps fast.
- Embed security into DevOps pipelines. Block builds that contain critical vulnerabilities before they reach production.
- Use hunts to showcase impact. A single campaign that pinpoints and removes 1,000 misprioritized exposures from the backlog is a sponsorship magnet.
- Translate risk into revenue language. Dashboards that map unpatched exposures to revenue-generating systems win board-level attention.
Follow these practices in sequence or parallel, guided by Zafran’s exposure management maturity model, and each cycle will compound your capacity to see, prioritise, and eliminate the exposures that matter most.
Zafran’s Solution in Action
- Unified Exposure Data Lake
Zafran ingests scanner feeds, EDR alerts, CNAPP findings, firewall rules, CMDB entries, and cloud telemetry into a normalized single source of truth that deduplicates redundant findings and prepares the data for automated reasoning. No more data siloes. No more seeing partial perspectives of an obscured truth. - Contextual Risk Engine
Automated analysis of internet exposure, runtime evidence, business tags, and compensating control coverage slashes false positives by up to 90 percent, surfacing the exposures most likely to be exploited. With better prioritization, your team can focus. - AI-Optimized RemOps
Generative AI merges overlapping remediation actions into a single “golden ticket,” adds precise remediation or compensating control guidance, and routes tasks through Jira or ServiceNow to the right owner. Hundreds of vulnerabilities solved with a single patch? Yes, please. - Exposure-Hunting Workbench
Analysts save hypotheses (e.g., “Log4Shell in runtime on internet-facing hosts”) and monitor residual exposure over time, transforming reactive patch sprints into proactive hygiene. - Executive-Ready Dashboards
Out-of-the-box visuals map exploitable exposure trends to revenue streams and risk appetite, giving CISOs a board-ready narrative without spreadsheet wrangling. Or build your own charts, the choice is yours.
Conclusion
Evolving to CTEM delivers on the promise of what vulnerability management should have been all along: find and fix your biggest risks, continuously. Better visibility and security findings enriched with real-world exploitability factors drive better prioritization. Automated validation proves exploitability. Automated response workflows help security teams compress exposure windows, focus on threats that truly matter, and articulate measurable risk reduction to leadership. Progress, not perfection, drives CTEM maturity, and with each incremental improvement your organization’s resilience grows.
Call to Action
Ready to reduce your exploitable vulnerability backlog by 90%? Request a personalized Zafran demo. Or explore the CTEM framework to plot your next step forward.
Internal Links
External Links
Request a demo today and secure your organization’s digital infrastructure.
