VM vs RBVM vs CTEM: What’s the Difference?
Ransomware crews now weaponize fresh CVEs in under a week, while regulators such as the EU’s NIS2 and the U.S. SEC demand risk-based cyber hygiene. Traditional vulnerability management (VM) alone struggles to keep up. This article clarifies how classic VM, risk-based VM (RBVM), and the emerging continuous threat-exposure management (CTEM) framework differ, where each excels or falls short, and how security teams can chart an evidence-based evolution path for 2026.

What is Vulnerability Management (VM)?
Vulnerability Management is the starting point for most organizations and is based on the foundational “scan-and-patch” cycle. The process is fairly simple: schedule a network or web scan, identify known Common Vulnerabilities and Exposures (CVEs), and patch them within a fixed SLA. An SLA, or Service Level Agreement, is a deadline set by the organization (for example, “critical issues must be patched within 30 days”) that defines how quickly vulnerabilities should be resolved.
Success in this model is usually measured by basic counts and timelines. Teams track the number of open versus closed vulnerabilities, calculate the average time to remediate (MTTR), or how long it takes on average to fix an issue once discovered, and monitor audit pass rates, which indicate whether they are meeting compliance requirements.
Prioritization in traditional VM leans heavily on the Common Vulnerability Scoring System (CVSS), which rates vulnerabilities on a scale from low (1.0–3.9) to medium (4.0–6.9), high (7.0–8.9), and critical (9.0–10.0). The problem is that CVSS scores don’t take into account the real-world context of the asset. As a result, teams are overrun by a flood of “critical” or “high” findings, many of which may not be exploitable or even relevant to the business. While VM helps organizations meet compliance checkboxes, it often overwhelms staff and wastes valuable time chasing noise instead of addressing the issues that truly matter.
What is Risk-Based Vulnerability Management (RBVM)?
Risk-Based Vulnerability Management represents the next level of maturity, building on the basics of VM but introducing a critical decision layer. Instead of treating every “critical” CVE as equally urgent, RBVM blends several factors to determine which issues truly pose the highest danger.
One of these factors is threat intelligence, which refers to real-world information about how attackers are behaving, such as whether a vulnerability is actively being exploited, if exploit code is available online, or if certain industries are being targeted. Another factor is asset criticality, meaning how important the affected system is to the business. For example, a vulnerability on an internal test server may not matter much, while the same issue on a payment-processing system could be catastrophic. Finally, exploit likelihood measures how probable it is that attackers could successfully take advantage of the vulnerability in practice.
Modern RBVM platforms take scanner output, enrich it with this intelligence and asset context, and generate a scored backlog that ranks issues by real risk. This allows security and IT teams to concentrate on the vulnerabilities most likely to lead to a breach, rather than spreading resources thin across thousands of theoretical “critical” issues.
What is Continuous Threat Exposure Management (CTEM)?
Unlike earlier models, CTEM expands discovery beyond just CVEs to include other types of weaknesses. These include misconfigurations (systems set up incorrectly in ways that create risk), privileged identities (user accounts with elevated permissions such as admin or root access that attackers often target), shadow IT (devices, apps, or cloud services deployed without central IT’s knowledge), and external attack-surface assets (systems visible to the internet that adversaries can probe directly).
Prioritization in CTEM is attack-path-centric, meaning it looks at how attackers would realistically move through the environment. For example, a medium-severity misconfiguration might allow lateral movement, where an attacker hops from one system to another, into a crown jewel database, the term for a system that holds highly sensitive or business-critical data, like customer financials or intellectual property. In CTEM, that misconfiguration would rank as more urgent than a “critical” CVE on an isolated lab server with no real business impact.
Validation is another feature that sets CTEM apart. Instead of assuming every theoretical weakness is exploitable, CTEM uses tools like breach and attack simulation (BAS), automated penetration testing, or control inspection to confirm whether a vulnerability can actually be exploited in the real environment.
Finally, mobilization orchestrates rapid response action. This doesn’t always mean waiting for a software patch; instead, it can quickly mitigate risk by changing the configuration or policies of existing defenses like a web application firewall (WAF), next-gen firewall (NGFW), or Endpoint Detection and Response (EDR) solution. By taking such swift mitigation action, the lengthy patching process is removed from the critical path so that organizations can shrink their exposure window and stay ahead of attackers.
So What Are The Key Differences Between VM, RBVM, and CTEM?
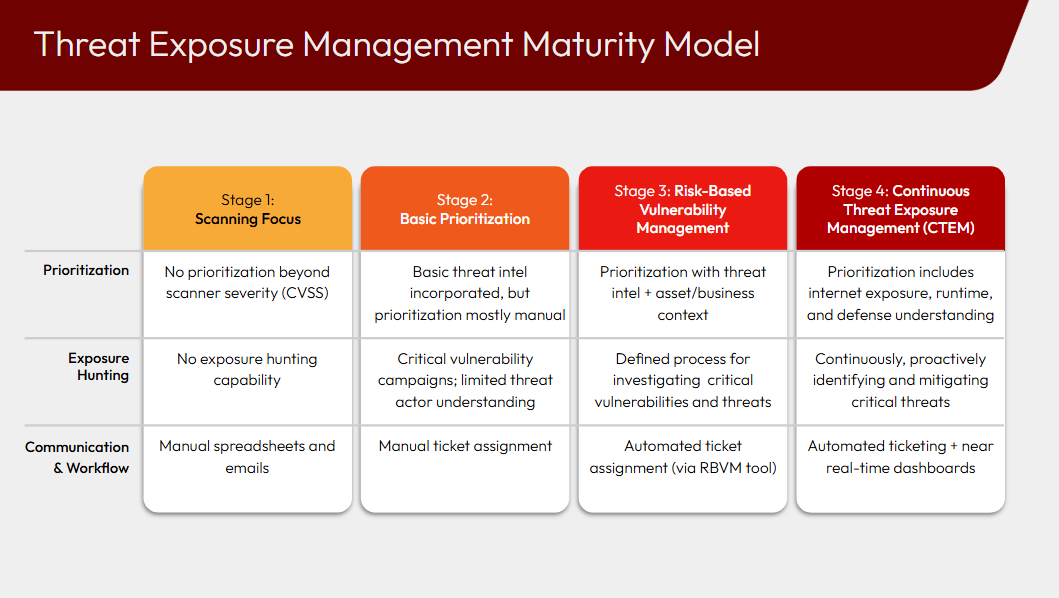
The progression from VM to RBVM to CTEM reflects a shift from volume-driven compliance to context-driven resilience, with each step representing a higher level of maturity.
- Vulnerability Management (VM) is the entry-level stage. It is primarily about detection and closure—it ensures scans are run, vulnerabilities are logged, and patches are applied within deadlines. The focus is on numbers, not nuance: how many vulnerabilities are open, how many are closed, and whether deadlines (SLAs) are met. What VM does not do is separate signal from noise; it treats all “critical” findings the same, regardless of business impact, leaving teams buried under alerts.
- Risk-Based Vulnerability Management (RBVM) represents an intermediate maturity level. It introduces risk-awareness by layering in threat intelligence and asset importance, helping teams distinguish the “must-fix” from the “nice-to-fix.” However, RBVM still has blind spots. It remains largely vulnerability-centric and siloed, focusing on CVEs without fully considering misconfigurations, identity weaknesses, or chained attack paths. It also lacks strong validation of whether a vulnerability is truly exploitable in the live environment.
- Continuous Threat Exposure Management (CTEM) is the most mature approach. It broadens the aperture to cover the full spectrum of exposures across identities, misconfigurations, and external attack surfaces. Unlike VM and RBVM, CTEM emphasizes validation by using simulations or control inspections to confirm what is actually exploitable. It also prioritizes mobilization, orchestrating rapid mitigation through existing defenses so exposures are reduced long before patching cycles are complete. What CTEM avoids is the trap of reporting without action; it closes the loop between detection and business risk reduction.
In short: VM tells you what’s broken, RBVM tells you what’s risky, and CTEM ensures you actually fix what matters most—continuously and in context.
Key Challenges Across the Three Models
Each stage in the evolution from Vulnerability Management (VM) to Risk-Based Vulnerability Management (RBVM) to Continuous Threat Exposure Management (CTEM) carries its own set of challenges and improvements. In the earliest model, VM, tool and data silos are a major obstacle: scanners, ticketing systems, and remediation tools rarely connect, leaving teams to piece together fragmented information. RBVM reduces this somewhat by blending scanner output with external intelligence, but silos persist. CTEM goes further by actively collapsing these gaps through unified data lakes and integrated workflows.
Another recurring issue is the exposure window, the dangerous time period between when a vulnerability is discovered and when it is patched. In VM, monthly or quarterly scans can leave exposures open for weeks. RBVM introduces faster alerting by incorporating threat feeds, but it is still largely dependent on periodic scans. CTEM changes the game with continuous discovery not only of exposures, but also control-based mitigations. Using your existing defenses, like firewall or endpoint rules, to dramatically and rapidly shrink exposure risk removes the lengthy patch process from the critical path of risk relief. CTEM makes this possible at scale. No more fumbling in the dark, searching for the right defensive measure. And, while patching is still good medicine, it is no longer the only weapon in your arsenal.
The balance of noise versus context also improves as models mature. VM floods teams with generic CVSS-driven alerts, many of which are not exploitable. RBVM reduces the noise somewhat by layering in threat intelligence and risk scoring, but it still surfaces vulnerabilities that may not pose real danger. CTEM applies contextual reachability and validation testing to confirm exploitability, slashing false positives and ensuring attention goes only to exposures that matter.
Process hand-offs remain another bottleneck. In VM, findings are dumped into ticket queues, leading to fatigue and inefficiency. RBVM provides clearer risk scores, but still generates large volumes of tickets that overwhelm IT teams. CTEM streamlines this with AI-optimized remediation planning, SLA tracking, and automated task assignment, so the right team gets the right task at the right priority level.
Finally, the models diverge in how they report business-level KPIs. VM emphasizes raw counts, such as the number of vulnerabilities closed or detected, and SLA compliance levels. RBVM may track trends in risk scores and asset criticality. CTEM goes much further, translating technical minutia into business risk management outcomes: exposure time reduction, risk trends, mitigated breach scenarios, and more.
Together, these differences highlight how VM begins with compliance-driven detection, while RBVM adds some nominal level of prioritization via threat intel. In contrast, CTEM fully operationalizes exposure management into a business-aligned risk reduction engine, prioritizing the most pertinent threats (via continuous analysis of internet exposure, runtime, and security defense comprehension) and mobilizing the most effective response actions for maximum impact.
Best Practices for 2026
To keep pace with modern threats, organizations must evolve their security operations from reactive patching to proactive exposure management. The following best practices illustrate not just what to do, but why each step is critical:
- Enrich Every Finding with Context. Raw scanner results alone overwhelm teams with thousands of “critical” vulnerabilities. By layering in runtime evidence, internet exposure, and exploit popularity, teams can separate the 10% of findings that truly matter from the 90% that are not exploitable. Without this context, prioritization becomes guesswork.
- Validate Controls Early. Simply assuming that defenses like WAFs, EDRs, or firewall rules are effective is risky. Automated policy inspection of these tools, in concert with specialized BAS, ensures those controls actually block the most dangerous attack paths. Early validation prevents false confidence and wasted effort.
- Automate Remediation Routing. Manual ticket creation leads to noise, duplication, and fatigue. By integrating with workflow platforms like Jira or ServiceNow and automatically deduplicating redundant patches into optimized tickets, organizations can drastically reduce the overhead of managing remediation work.
- Measure Exposure Reduction, Not Patch Volume. Counting closed vulnerabilities or patch rates doesn’t reflect actual risk reduction. Instead, the focus should shift to metrics like mean time to mitigate exploitable attack paths, which better capture how well teams are shrinking adversary opportunity windows.
- Run Quarterly CTEM Sprints. Continuous Threat Exposure Management (CTEM) is most effective when run as a cycle of continuous learning. These sprints across the five stages (scope, discover, prioritize, validate, and mobilize) allow organizations to expand coverage, refine metrics, and steadily improve risk management.
Zafran’s Solution

Zafran was designed specifically to tackle these challenges by embedding best practices into a unified, AI-powered threat exposure management platform. Each capability directly addresses the exact pain points that hold organizations back today:
- Filter Noise with Contextual Intelligence. Zafran ingests scanner, cloud, identity, and endpoint signals without requiring new agents, creating a unified picture of exposures across the enterprise. It then layers in runtime evidence, verifying whether the vulnerable component is actually running in memory, as well as internet reachability checks to determine if the asset is externally exposed and therefore more attractive to attackers. On top of this, Zafran validates compensating controls such as WAF rules or firewall policies to confirm whether the vulnerability is already mitigated by existing defenses. By combining runtime presence, internet-facing exposure, and control validation, Zafran proves that up to 90% of “critical” findings are not actually exploitable. This level of precision cuts through the noise and ensures security teams spend their limited time on the exposures that truly matter.
- Mitigate Fast with Control-Based Actions. Zafran doesn’t make you wait weeks for a vendor patch. Instead, it tells you exactly which existing defenses, such as WAF, EDR systems, or firewall access control lists (ACLs), should be updated to block the threat immediately. By neutralizing high-risk exposures within hours, Zafran closes the dangerous “exploit-to-patch” gap and reduces organizational risk in real time.
- RemOps Engine for Smarter Workflows. Zafran’s generative AI deduplicates overlapping CVEs, bundles them into single high-fidelity “golden tickets,” and auto-routes them into Jira or ServiceNow with clear, actionable instructions. This automation eliminates ticket fatigue and guarantees the right fix lands with the right team.
- Executive Dashboards for Business Alignment. Zafran translates complex technical metrics into board-ready insights, such as exposure-time curves and progress against risk appetite. This enables leadership to see measurable risk reduction, not just patch counts, driving informed strategy and investment decisions.
By directly addressing the problems of noise, delays, workflow fatigue, and poor visibility, Zafran transforms CTEM mobilization from an aspirational goal into an operational reality.
Conclusion
VM, RBVM, and CTEM represent a maturity curve from reactive patching to proactive, continuous risk reduction. VM supplies essential hygiene; RBVM aligns fixes to business risk; CTEM closes the loop with validation and rapid mobilization. As exploit windows shrink to days, organizations that remain in VM-only mode risk drowning in alerts and missing the few exposures that matter. By layering contextual prioritization today and iterating toward a CTEM program, security leaders can cut exploitable vulnerability backlogs by double-digit multiples and demonstrate real risk reduction to the board.
