
Blog
Yonatan Keller
The “Agentic Trojan Horse” Debate: How OpenClaw’s Convenience Model Opens Real-World Attack Paths
February 17, 2026

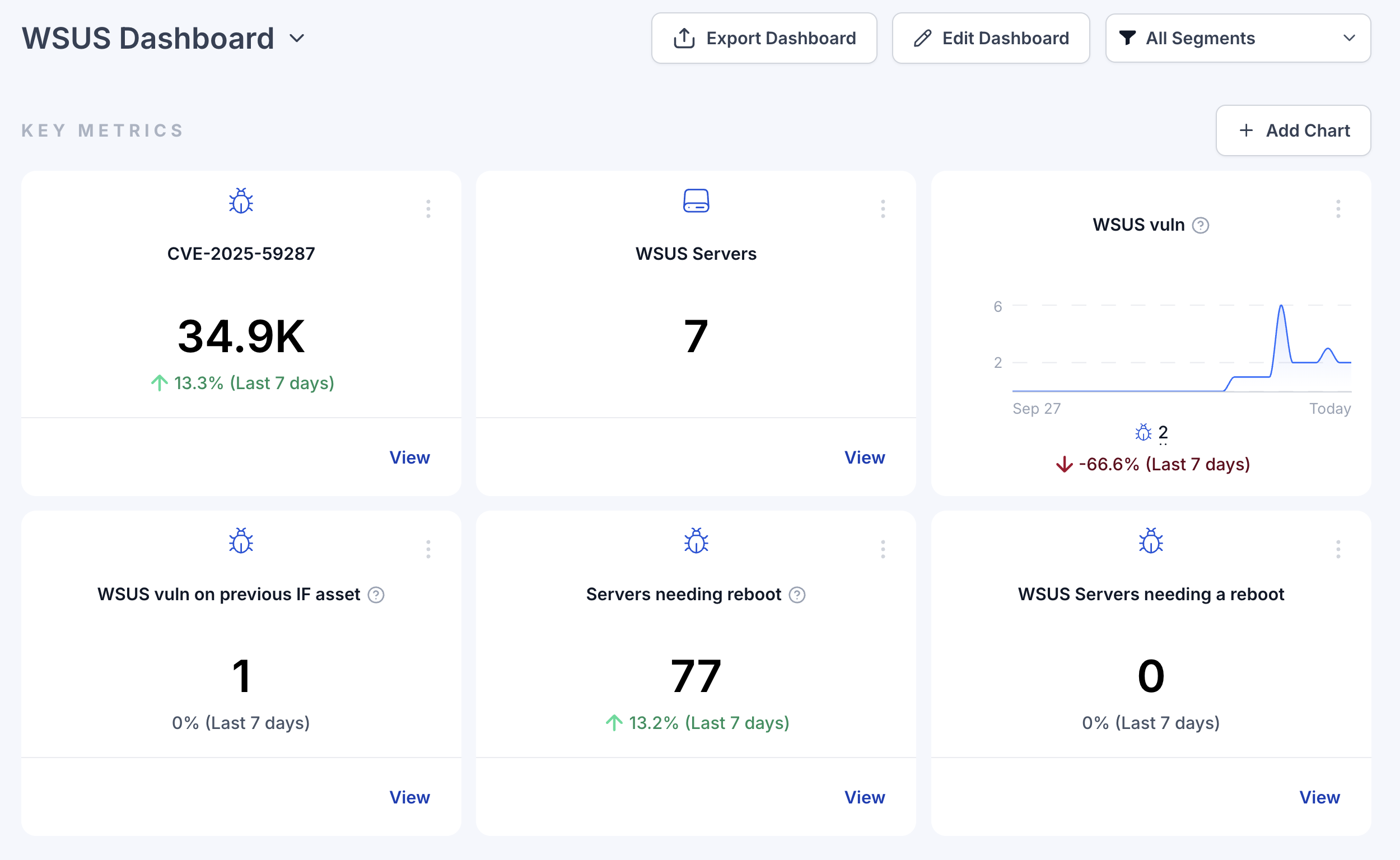
CVE-2025-59287 is a critical deserialization of untrusted data vulnerability that allows an unauthorized attacker to execute code on vulnerable machines by sending a specially crafted event to the WSUS server without any user interaction required. The vulnerability stems from insecure deserialization when WSUS improperly deserializes untrusted objects, allowing attackers to send specially crafted requests to the WSUS service.
Only Windows Server systems with the WSUS Server Role enabled are affected; servers without that role are not vulnerable.
Supported affected families include Windows Server 2012/2012 R2/2016/2019/2022/23H2/2025 prior to the out-of-band updates listed below.
Corresponding KBs: 2025 (KB5070881), 23H2 (KB5070879), 2022 (KB5070884), 2019 (KB5070883), 2016 (KB5070882), 2012 R2 (KB5070886), 2012 (KB5070887).
To exploit the vulnerability, an attacker would have to:
Attacks might result in:
Here are a few recommendations on how to mitigate the risk of CVE-2025-59287:
Hunting this vulnerability with Zafran compresses time-to-risk-reduction aligned to the CTEM process.
First we first scope the environment by automatically enumerating every server with the WSUS role across on-prem and cloud estates, helping to validate whether the specific vulnerable processes are run on an exposed server. We then facilitate prioritization by weighting exposures using context such as internet reachability (identifying the specific open ports) and runtime presence (is it loaded in memory). Relying simply on scanner findings will likely result in several false positives, so it is important to consider this context for prioritizing what is truly a risk in your environment.
Further, Zafran will automatically provide specific mitigations against CVE-2025-59287, leveraging new rules by your security vendors, once issued. And finally, Zafran mobilizes closure by helping its customers to assign accountable owners, enforce SLAs, and track patching processes within their organization.
Traditional vulnerability management must change. So many are drowning in detections, and still lack insights. The time-to-exploit window sits at 5 days. Implementing a Continuous Threat Exposure Management (CTEM) program is the path forward. Moving from vulnerability management to CTEM doesn't have to be complicated. This guide outlines steps you can take to begin, continue, or refine your CTEM journey.
