How to Detect and Mitigate the Critical WSUS Exploit (CVE-2025-59287)

Summary
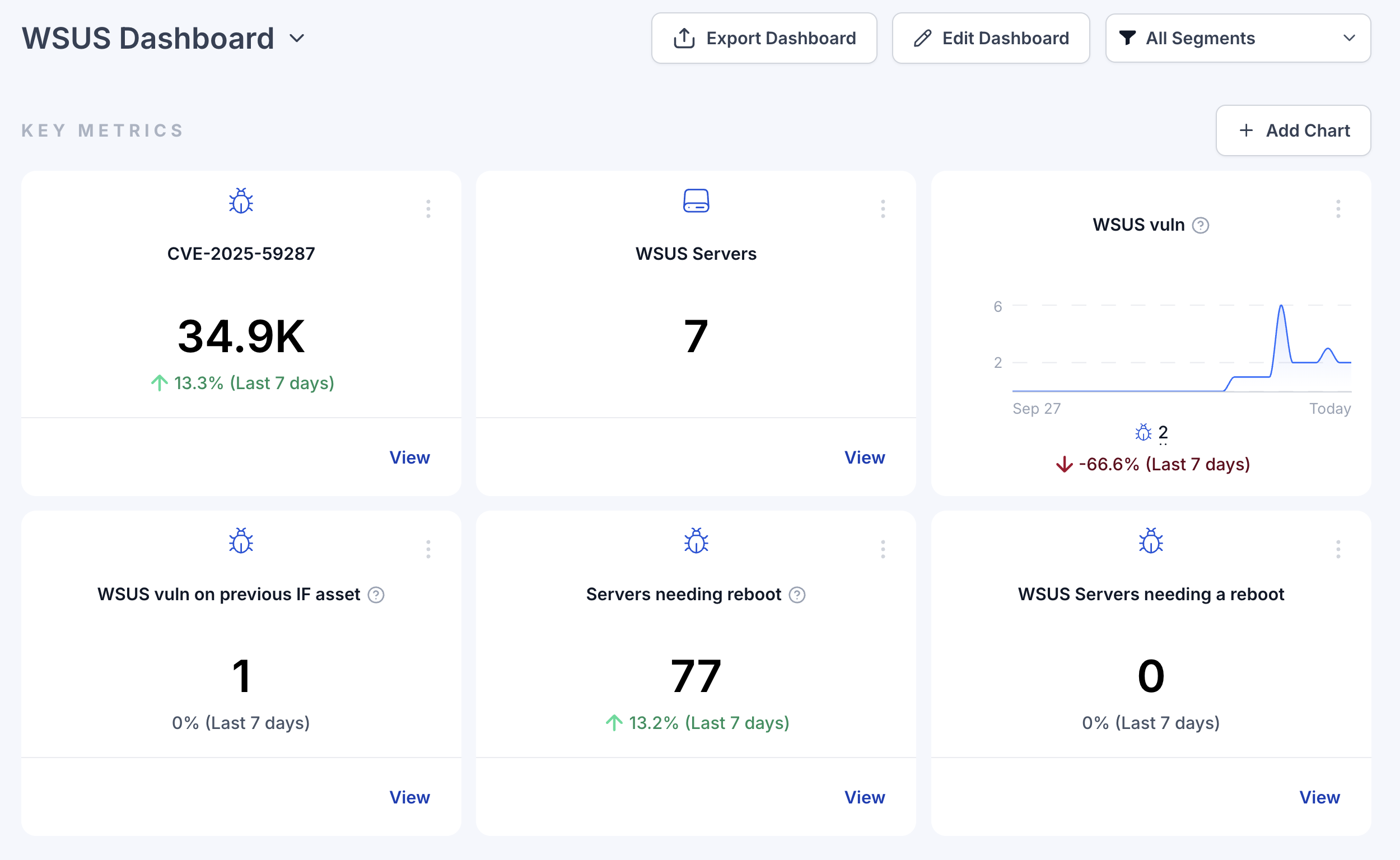
CVE-2025-59287 is a critical deserialization of untrusted data vulnerability that allows an unauthorized attacker to execute code on vulnerable machines by sending a specially crafted event to the WSUS server without any user interaction required. The vulnerability stems from insecure deserialization when WSUS improperly deserializes untrusted objects, allowing attackers to send specially crafted requests to the WSUS service.
Timeline
- October 14, 2025: First disclosure, Microsoft documents and fixes the issue as part of Patch Tuesday.
- October 20-21, 2025: Proof-of-Concept published by cybersecurity researchers and vendors.
- Oct 23–24, 2025: Microsoft releases emergency updates for supported Windows Server versions to accelerate remediation.
- October 24, 2025:
- Active Exploitation Confirmed by the Dutch National Cyber Security Centre within hours of the PoC release.
- CISA adds CVE-2025-59287 to the Known Exploited Vulnerabilities (KEV) catalog
Affected Versions
Only Windows Server systems with the WSUS Server Role enabled are affected; servers without that role are not vulnerable.
Supported affected families include Windows Server 2012/2012 R2/2016/2019/2022/23H2/2025 prior to the out-of-band updates listed below.
Corresponding KBs: 2025 (KB5070881), 23H2 (KB5070879), 2022 (KB5070884), 2019 (KB5070883), 2016 (KB5070882), 2012 R2 (KB5070886), 2012 (KB5070887).
Attack Characteristics
To exploit the vulnerability, an attacker would have to:
- Reach a WSUS server over the network (commonly TCP 8530/HTTP or 8531/HTTPS).
- Send crafted requests to WSUS reporting web services that trigger unsafe object deserialization in a legacy mechanism, leading to RCE as SYSTEM.
- Observed attacks used multiple POSTs and spawn cmd.exe/PowerShell for recon. Exploitation includes spawning Command Prompt and PowerShell via the HTTP worker process, with base64-encoded payloads used to enumerate sensitive network and user information.
- No authentication or user interaction needed.
- Under certain conditions, compromised WSUS servers might distribute malicious updates to all managed endpoints. For that purpose:
- Third-party/local publishing needs to be enabled and clients trust the WSUS signing certificate.
- WSUS/clients use HTTP (no TLS), enabling on-path tampering/spoofing to serve “updates” or alter command-line parameters of signed installers.
Attacks might result in:
- Full takeover of the WSUS host (SYSTEM).
- Potential wormability between WSUS servers and risk to the update supply chain inside the org (abuse of WSUS to push malicious packages).
Mitigation Recommendations
Here are a few recommendations on how to mitigate the risk of CVE-2025-59287:
- Patch immediately by installing the out-of-band KB for your Windows Server version (see list above). Reboot after install; you do not need prior cumulative updates.
- If you cannot patch right now, apply a temporary workaround: disable the WSUS Server Role, or block all inbound traffic to ports 8530 and 8531 on the host/firewall. Understand this will interrupt update delivery from WSUS. Restore service only after patching.
- Reduce exposure by ensuring WSUS is not internet-facing and is reachable only from trusted management subnets.
- Detect with SNORT: Snort 2 (GID 1, SID 65422) and Snort 3 (GID 1, SID 65422).
- Validate the environment after patching. Microsoft notes a deliberate behavior change: WSUS no longer shows synchronization error details after installing these updates.
- Hunt for signs of compromise around Oct 20–26 and going forward: unusual access to 8530/8531, anomalous cmd.exe or PowerShell spawned by WSUS worker processes, and unexpected outbound connections from WSUS hosts.
How can Zafran help
Hunting this vulnerability with Zafran compresses time-to-risk-reduction aligned to the CTEM process.
First we first scope the environment by automatically enumerating every server with the WSUS role across on-prem and cloud estates, helping to validate whether the specific vulnerable processes are run on an exposed server. We then facilitate prioritization by weighting exposures using context such as internet reachability (identifying the specific open ports) and runtime presence (is it loaded in memory). Relying simply on scanner findings will likely result in several false positives, so it is important to consider this context for prioritizing what is truly a risk in your environment.
Further, Zafran will automatically provide specific mitigations against CVE-2025-59287, leveraging new rules by your security vendors, once issued. And finally, Zafran mobilizes closure by helping its customers to assign accountable owners, enforce SLAs, and track patching processes within their organization.
References
- Microsoft Support KB - https://support.microsoft.com/en-us/topic/october-23-2025-kb5070883-os-build-17763-7922-out-of-band-860bc03c-52fb-407c-89b2-14ecf4893c5c
- https://www.bleepingcomputer.com/news/security/microsoft-releases-windows-server-emergency-updates-for-critical-wsus-rce-flaw/
- https://nvd.nist.gov/vuln/detail/CVE-2025-59287?utm_source=chatgpt.com
- https://thehackernews.com/2025/10/microsoft-issues-emergency-patch-for.html
- https://www.securityweek.com/critical-windows-server-wsus-vulnerability-exploited-in-the-wild/
Traditional vulnerability management must change. So many are drowning in detections, and still lack insights. The time-to-exploit window sits at 5 days. Implementing a Continuous Threat Exposure Management (CTEM) program is the path forward. Moving from vulnerability management to CTEM doesn't have to be complicated. This guide outlines steps you can take to begin, continue, or refine your CTEM journey.

Request a demo today and secure your organization’s digital infrastructure.
Request a demo today and secure your organization’s digital infrastructure.



