Is ‘Vibe Patching’ the future of Vulnerability Management?
Zafran Labs presents a blueprint for agentic remediation.

AI hype is all around – AI is the new ‘digital’, the new ‘cloud’, the new ‘mobile’, the new new. And while a lot of it is just hot air, some real opportunities are emerging - from fast coding, to smarter searches, to better planning, and a tidal wave of summarized content in every corner of our digital lives (‘agentic’ lives, come to think of it 🙄).
Unfortunately, attackers are also adopting the trend. In a recent blog, Check Point detailed how hackers used the newly released HexStrike-AI framework to exploit fresh NetScaler zero-days - compressing the time-to-exploit window to unprecedented levels. Anthropic has reported that its Claude model was weaponized in real-world breaches, helping attackers write code that exfiltrated data from at least 17 organizations. And the Chinese group Aquatic Panda has been observed using LLMs to debug exploit code, refine evasion scripts, perform reconnaissance, and achieve persistence. These examples illustrate how AI is not only accelerating the speed of attacks but also enhancing their sophistication and stealth, creating serious challenges for defenders.
So can AI also help counter these AI‑driven advances? Are today’s LLMs, and their emerging "agentic" capabilities, mature enough to investigate impact, assess dependencies, and generate ready‑to‑use remediation scripts for a large portion of enterprise vulnerabilities?
Zafran Labs – the research team at Zafran dedicated to dissecting vulnerabilities, assessing exposures, and continuously developing the Zafran Exposure Graph – set out to answer this question. In this blog, we’ll present a sneak peek into the development of Zafran’s own Agentic AI tool, aimed at investigating, assessing and remediating enterprise vulnerabilities.
Our initial experiments and the overall statistics we’ve analyzed (which includes many large enterprises, with millions of assets), show promising results: when current agentic models are paired with a rich vulnerability data warehouse and a secure, real-time way to interact with affected assets, they can fundamentally change the remediation game - a shift that defenders urgently need as attackers gain AI-powered momentum.
But first, let’s look at where the “remediation game” stands today. While most enterprises have embraced the cloud, the majority of assets - 72% in our data - are still on-prem (endpoints, servers, unmanaged devices). Only 14% are container images. In practice, this means most enterprise assets are maintained and patched with a shift-right approach. The reality: enterprises, by and large, have not yet shifted left.
In a shift-right remediation approach, vulnerability analysts face multiple manual and tedious steps. Traditional vulnerability management tools often provide generic “remediation steps,” but in practice, these are rarely actionable out of the box. Many vulnerabilities are configuration-specific, and some aren’t patchable at all - either because no vendor fix exists or because applying a patch could introduce significant operational risk due to dependencies. Analysts must go back to the source: understanding how each vulnerability truly impacts an asset, whether configuration-specific conditions apply, whether a patch is available, and what dependent processes or components would be affected.
The nature of software vulnerabilities makes these steps inherently non-deterministic - each vulnerability may require a different validation approach, each patch may need to be simulated differently. And, as it turns out, non-determinism is at the heart of agentic AI - for better, or for worse. Let’s see how we tame the beast.
Developers who have used Cursor, Claude‑Code, or other AI coding tools know how they succeed: they read existing code, write a change, compile and test it, analyze failures, and iterate. Any effective AI agent, today, requires a closed-loop system, to move from ‘maybe works’ to ‘works’. The same applies to Agentic Remediation.
Diagram:
Four ingredients for making an effective Remediation Agent:
- Great Exposure Context Data
- A scalable and efficient way to query that data
- Real-time interface to run (read-only) commands on vulnerable assets, validate assumptions, and generate ready-to-use remediation scripts
- Lastly, but most importantly - a User; A human-in-the-loop, to approve execution of commands, and ask the right questions
Data:
AI agents are only as effective as the data they have access to. Leveraging the rich context and detailed knowledge graph within the Zafran platform, an AI agent can hunt for the most exploitable vulnerabilities that are found in-runtime, understand business-context, validate reachability risk (e.g., Internet-facing exposures), and identify the underlying components that need fixing.
Scale:
Exposure management is fundamentally a data problem - and therefore also a scale problem. A mid-sized enterprise typically manages ~100,000 assets, each with ~1,000 vulnerabilities spread across ~1,000 unique software components. These numbers compound quickly: the result is roughly 100 million vulnerability findings at any given time. Humans simply cannot sift through this volume, and AI models face context limitations as well. Solving this challenge requires two elements: a scalable and reliable data warehouse, and an efficient method to query it. In our lab, we paired our agent with the MCP server of our platform’s data warehouse for our Zafran tenant. The agent quickly learned the warehouse’s data structures and effectively queried the most relevant data. Many “agentic” solutions are merely strapped onto existing APIs, which are often slow and inefficient. With query-level access, an agent can leverage the full power of a high-performance analytical database to locate the information it needs.
Real-time interface:
Once an agent identifies a critical exposure, gathers context, and obtains initial guidance from vulnerability scanners, it must investigate the issue live. Using Zafran’s patented technology to run inspection scripts through existing agents, the closed-loop system allows the AI to assess and test potential fixes. Through iterative exploration, the agent reaches a conclusion: a detailed report explaining whether a vulnerability can be patched, and, when possible, a ready-to-use remediation script.
User:
A user, to guide and authorize actions is an integral part of an agentic remediator - required to
Title: Agentic Remediation Architecture
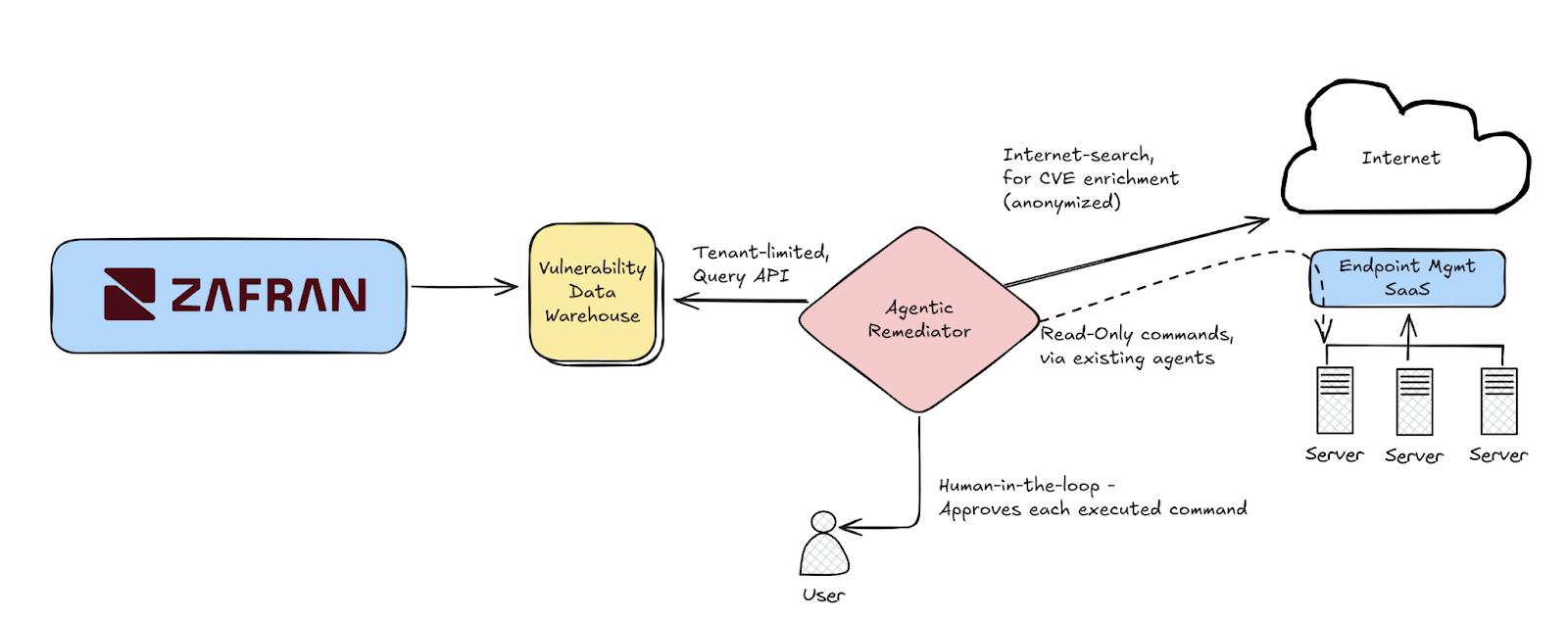
The architecture above summarizes the 4 ingredients for creating an Agentic Remediator, and the POC demos below show it action:
POC demo video 1:
- Shows the agent hunting for an exploitable CVE in an Internet-exposed asset
- Shows the agent finding the vulnerable component on that asset (via our data)
- Asks the user permission to connect to the machine to investigate the exposure
- A terminal is popped-up, and the agent asks the user permission to run a few commands (per-command)
- Lastly, the agent produces a detailed report with how the vulnerability can be remediated, shows the required commands to run, and asks the user if he wants it to run them
- It runs the commands
- It runs commands that show the package has been fixed, thus the vulnerability has been remediated
POC demo video 2:
- Very similar to the above, however , the agent finds there is no patch available in the package manager, but it goes further and investigates configuration of the vulnerable component and finds that the vulnerability is NOT exploitable in the current settings and produces a report
POC demo video 3:
- Very similar to the above, where no patch is available, configurations show that the component is in an exploitable setting. The agent offers a configuration mitigation and the user allows it to apply them, and the agent then provides a report on how the vuln is now not exploitable
These demos illustrate how an agentic remediator can automate vulnerability handling in multiple scenarios: applying a straightforward fix, proving a vulnerability is non-exploitable due to configuration, or guiding a safe configuration-based mitigation.
While these tests focused on Linux-based findings, the context is critical: According to Zafran’s data 67% of enterprise vulnerabilities affect Linux assets, even though Linux makes up only 27% of assets (with Windows at 47%). This is explained by the fact that on average, Linux assets carry three times more vulnerabilities than Windows. Digging deeper, package-manager vulnerabilities represent 71% of Linux findings, with another 15% tied to third-party Java dependencies (such as Log4j). By focusing remediation agents with targeted prompts and tools to specialize in investigating and remediating package-manager based vulnerability findings, we achieved the successful outcomes highlighted above.
Looking ahead, we believe this approach can expand across other remediation “classes.” Yes, every patch is a snowflake, but recognizable patterns do emerge. Over time, these patterns could enable remediation agents to automate much of the work vulnerability analysts perform today - who may soon find themselves “vibe-patching” with AI assistance.
Scaling this approach, and connecting the dots between AI-generated remediation scripts, with automated patching solutions- would bring us one step closer to real-world automated remediation.
Our next step at Zafran is taking this approach from blueprint to production. The key challenge: evolving a non-deterministic agent into an enterprise-ready system. This requires strict security and safety guardrails - principles we embed into every technology we develop. That’s even more critical as we explore solutions that not only leverage AI, but give it (some) agency in service of enterprise defense.
Request a demo today and secure your organization’s digital infrastructure.
Request a demo today and secure your organization’s digital infrastructure.
