SAP servers under attack - Security and Data vendors targeted - 1/3 of initial accesses gain via exploitation

Initial Access Broker targets a critical SAP zero-day
A critical zero-day in SAP NetWeaver (CVE-2025-31324) is exploited in the wild and compromised over 400 servers worldwide. The flaw allows unauthenticated attackers to upload malicious binaries on a host system. It has been abused to drop a webshell resulting in payload deployment, code execution and lateral movement. Based on an observed few days gap between initial access and post-compromise operations, it is estimated that the zero-day was leveraged by an initial access broker. SAP NetWeaver is the runtime environment for all SAP applications and more than 10K internet-facing hosts are considered vulnerable globally.

[mitigate]Restrict access to the /developmentserver/metadatauploader endpoint and turn Visual Composer off[/mitigate]
ToyMaker exploits flaws and provide initial access to Cactus ransomware
The infamous ransomware group Cactus apparently works with an initial access broker nicknamed ToyMaker. The threat actor gains initial access through a wide range of known vulnerabilities in Internet-facing unpatched systems. It then deploys LAGTOY custom malware, able to extract credentials or execute commands on compromised hosts.
Operation SyncHole targets zero-days in enterprise software
In a new campaign dubbed “Operation SyncHole”, The prominent North Korean group Lazarus is targeting South Korean organizations with various zero-days, including in Cross EX and Innorix. The flaws were leveraged to deploy malware in post-compromise stage, while initial access was enabled through the redirection of targeted users from infected websites. Cross EX is a security tool common in South Korean large companies and aimed at ensuring security controls are running in browser environments. Innorix is a South Korean software for enterprise AI and file sharing.

Craft CMS exploitation against many websites
Two critical zero-days in Craft CMS (CVE-2025-32432, CVE-2024-58136) were chained together with the purpose of gaining initial access to web servers and uploading a PHP file manager. The exploitation apparently resulted in data exfiltration and the deployment of backdoors in hundreds of servers.
[mitigate]Run the php craft setup/security-key command and copy the updated CRAFT_SECURITY_KEY environment variable to all production environments; Block access from 103.106.66[.]123, 172.86.113[.]137, 104.161.32[.]11, 154.211.22[.]213 and 38.145.208[.]231[/mitigate]
Marks & Spencer caught in Scattered Spider's web
Scattered Spider launched a wide scale ransomware attack on the popular British retail firm Marks & Spencer (M&S), resulting in the cessation of all online shopping and in hundreds of logistics workers required to stay home. Last February, the threat group stole a Windows domain's NTDS.dit file, cracked the included password hashes for Windows accounts and laterally spread before deploying the DragonForce ransomware on ESXi hosts. Scattered Spider is an English-speaking network of hackers (partly composed of American teenagers) deploying various ransomware strains and known for its wide attack on MGM Resorts in 2023. While skilled mostly in sophisticated social engineering tactics, it has also been spotted exploiting a vulnerability in ESXi Hypervisors (CVE-2024-37085).

A ransomware recovery company targeted by a ransomware
The remote and support operations of Hitachi Vantara were widely disrupted as servers were taken offline following an Akira ransomware attack. The Hitachi subsidiary offers data storage, cloud management and ransomware recovery services to large corporates and governments. Akira is a notorious Russian triple extortion group that has impacted more than 250 organizations and earned 42 million USD since 2023. While using various initial access methods, the group has recently put an accent on targeting ESXi vulnerabilities.
Large concerns around Commvault's critical flaw
Wide concerns emerged following the publication of a POC exploit for a flaw in Commvault’s command center (CVE-2025-34028)- a popular web-based platform providing backup and recovery services, as well as cloud storage and data protection, to over 100K customers worldwide including many Fortune 500 companies. The vulnerability is a Server-Side Request Forgery (SSRF) flaw allowing an unauthenticated attacker to upload malicious ZIP files in a command center environment and resulting in its full compromise. In the meantime, another Commvault vulnerability (CVE-2025-3928), letting authenticated attacker to create webshells, has been observed as exploited in the wild.

Apply Checkpoint IPS rule “Commvault Command Center Remote Code Execution”
When threat actors target security vendors
SentinelOne reveals that PurpleHaze, a Chinese group with ties with APT15, has been targeting the company’s infrastructure since 2024. After exploiting known vulnerabilities in Checkpoint Gateway, the threat actor deployed a backdoor in various organizations including an entity supporting a South Asian government and a company providing hardware logistics for SentinelOne employees. The security vendor has also defended against sophisiticated social engineering campaigns from DPRK state actors and Russian ransomwares.
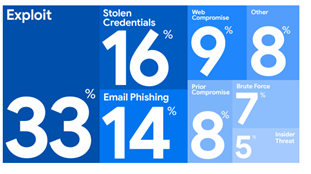
Exploitation represents one third of initial access attacks
A new report based on over 450 hours of investigations shows that in 2024 vulnerability exploitation represented a third of initial accesses, far before stolen credentials (16%) and phishing (14%). However, in ransomware operations, brute force was the most popular tactic (26%), followed by both stolen credentials and vulnerability exploitation (21% each). The most commonly exploited vulnerabilities have been in PAN-OS GlobalProtect (CVE-2024-3400), Ivanti Connect Secure (CVE-2023-46805, CVE-2024-21887) and FortiClient EPM (CVE-2023-48788).
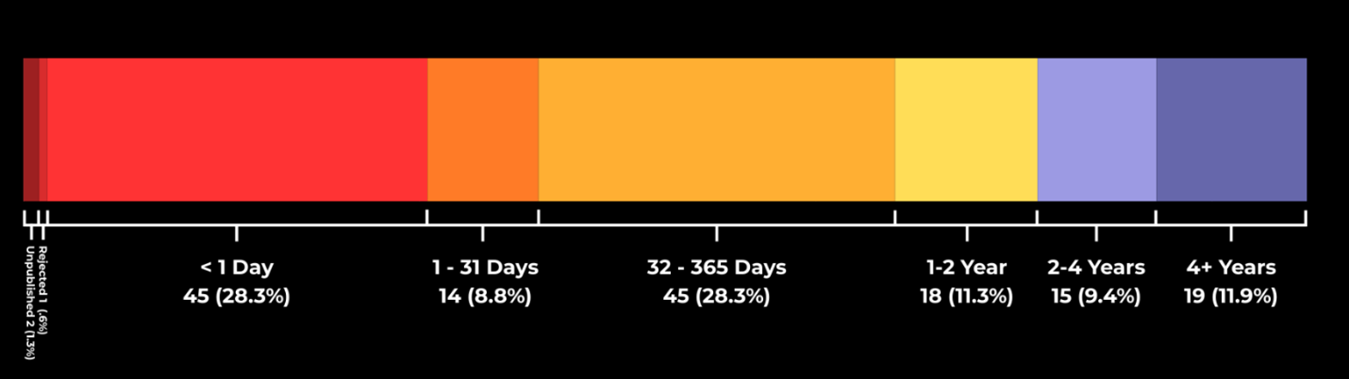
159 new exploited vulnerabilities in 2025 H1
Another report reveals that 159 vulnerabilities have been tagged as exploited in the wild in the first half of 2025 – 45 of them (28%) being exploited within one day since their disclosure. 35 of these vulnerabilities exist in Content Management Systems, 29 in Network Edge Devices and 24 in Operating Systems. A quarter of these exploited flaws are still waiting for NIST enrichment, and a large proportion had a medium CVSS/EPSS medium score despite being exploited in the wild.
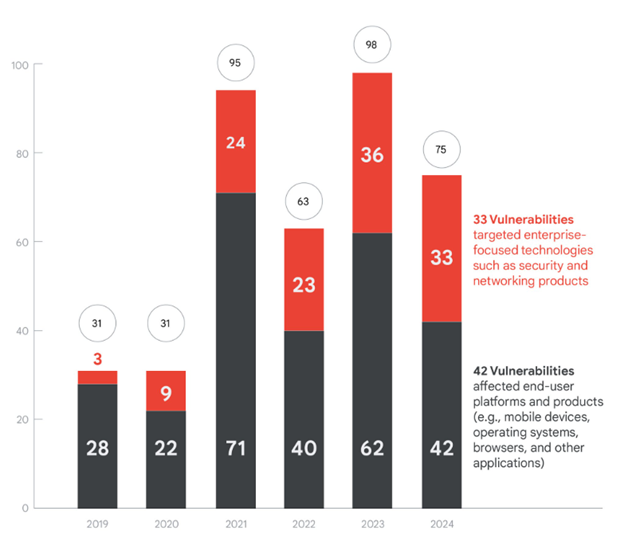
Zero-day exploitation focuses on security software and network devices
A new study listed 75 vulnerabilities which were exploited before been patched in 2024, a decrease from 98 that were found in 2023. 20 of them (60% of enterprise technologies' vulnerabilities) were targeted in security software and devices. Furthermore, Windows exploited-before-patch vulnerabilities jumped from 16 to 22. On the other hand, exploitation in browsers and mobile devices declined, following improvements in mitigation technologies.
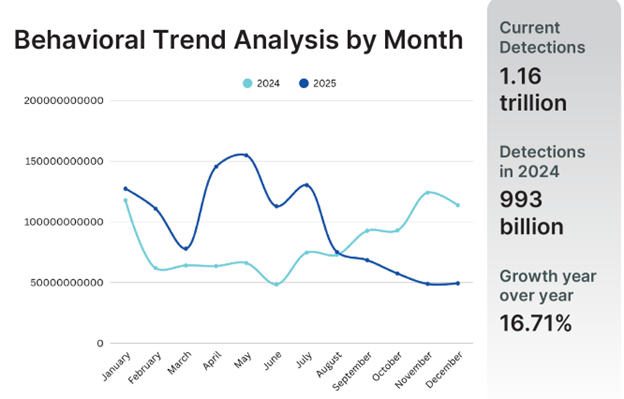
97 billion automated exploitation attempts in 2024
Fortinet has recorded in 2024 a record high number of 97 billion automated exploitation attempts. The most targeted vulnerabilities were in Netisrouters (CVE-2019-18935), GoAhead Cameras (CVE-2017-18377) and Zyxel Firewalls (CVE-2022-30525). In average, it took attackers 5.4 days to initiate exploitation after a vulnerability disclosure. Wide scale reconnaissance campaigns, fueled by the use of AI tools and the rise of Initia Access Brokers, also led to an unprecedented volume of 1.16 trillion detections of active scanning.
Heading 1
Heading 2
Heading 3
Heading 4
Heading 5
Heading 6
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.
Block quote
Ordered list
- Item 1
- Item 2
- Item 3
Unordered list
- Item A
- Item B
- Item C
Bold text
Emphasis
Superscript
Subscript
Mitigate
Heading 1
Heading 3
Heading 2
Heading 4
Heading 5
Heading 6
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.
Block quote
Ordered list
- Item 1
- Item 2
- Item 3
Unordered list
- Item A
- Item B
- Item C
Bold text
Emphasis
Superscript
Subscript