RegreSSHion exposes millions of Linux OpenSSH servers - Cisco switches actively exploited

RegreSSHion
Qualys has discovered the RegreSSHion vulnerability (CVE-2024-6387),which potentially exposes millions of Linux OpenSSH servers to complete system takeover. The flaw arises from a signal handler race condition in sshd, which could allow attackers to execute arbitrary code with root privileges and consequently to install malware, deploy backdoors, or manipulate data. While first exploits were published only a few hours after Qualys’s disclosure, there are so far no confirmed active exploitations of the vulnerability. Exploitation is considered relatively complex, and it requires an average of 6 to 8 hours of multiple attempts, during which the attack may fail due to brute-force protection tools. Read more in Zafran’s latest blog.

[mitigate]Set the LoginGraceTime to 0 in the sshd configuration file; make sure your brute force protection features are installed and updated; Detect with Tenable plugins 201194, 201211-14, 201219-20, 201228, 201301-2, 201328, 201551.[/mitigate]
Velvet Ant attacks Cisco switches
Since last April, the Chinese Velvet Ant has been exploited a zero-day in Cisco Nexus switches (CVE-2024-20399) to deploy remote access malware. The vulnerability is a command injection flaw in NX-OS systems allowing authenticated local attackers to run commands as root. It also lets the attacker to avoid triggering system log messages. Velvet Ant is a recently discovered sophisticated group, behind a campaign targeting a large organization while leveraging vulnerabilities in out-of-life F5 Big-IP devices for long term persistence.

[mitigate]Apply Qualys QID 317465.[/mitigate]
A new flaw in EOL WiFi routers
A new vulnerability in D-Link DIR-859 WiFi routers (CVE-2024-0769) is being exploited in the wild. The vulnerability is a path traversal flaw in the routers’ HTTP POST request handler component. The vendor stopped supporting this product line four years ago and will not patch the flaw.
IntelBroker publishes new breaches
IntelBroker put on sale a database from Virginia’s Department of Elections, 40,000 users’ information from the IT consulting company Cognizant and source code stolen from a Mexican bank. The actor is known for focusing on vulnerability exploitation and has recently allegedly leveraged a Jira zero-day.
Rhysida attacks a children hospital
LastJanuary, Rhysida exfiltrated 800,000 personal records from a Chicago children’s hospital, leading some of its systems to be taken offline. Following the hospital‘s refusal to pay any ransom, the data has apparently been sold online. Rhysida is a "ransomware as a service" provider known for exploiting VPN vulnerabilities as the ZeroLogon flaw (CVE-2020-1472).

Old MSHTML flaw under exploitation
A three-year-old Microsoft MSHTML vulnerability (CVE-2021-40444) is being exploited to deliver a surveillance tool against targets in the US, Canada, Poland and India. The flaw is triggered when the victim clicks on a Word document containing a fake job description. The vulnerability allows code execution, and in this case was used to redirect the user to a malicious html page.
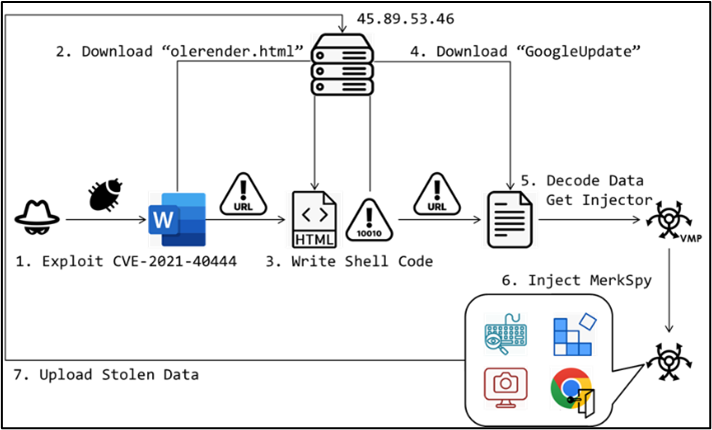
[mitigate]Select the detection build 1.349.22.0 in Microsoft Defender for Endpoint.[/mitigate]
APT29's intrusion into TeamViewer
The Russian APT29 has infiltrated the internal IT environment of TeamViewer, a famous connectivity platform firm. The company claimed that the production environment, customer data and the platform itself were not affected, thanks to network segmentation that segregates the corporate IT network from other subnets. APT29 gained initial access to TeamViewer environment with stolen credentials from a former IT employee.
Hubspot data breach
Threat actors are leading a campaign targeting HubSpot customers and, despite the company’s detection and mitigation efforts, they succeeded to compromise t least 50 accounts. Hubspot is a well-known enterprise software for sales and marketing teams.

The new Microsoft's vulnerability reporting policy
Microsoft announced it will now assign CVE IDs to vulnerabilities in its cloud products. Vulnerabilities will be published if they are potentially harmful or if they require action from customers and third parties. The policy change takes place in the context of Microsoft’s Secure Future Initiative (SFI), aiming at increasing transparency in an attempt to address the recent criticism about the company’s cybersecurity strategy.
Heading 1
Heading 2
Heading 3
Heading 4
Heading 5
Heading 6
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.
Block quote
Ordered list
- Item 1
- Item 2
- Item 3
Unordered list
- Item A
- Item B
- Item C
Bold text
Emphasis
Superscript
Subscript
Mitigate
Heading 1
Heading 3
Heading 2
Heading 4
Heading 5
Heading 6
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.
Block quote
Ordered list
- Item 1
- Item 2
- Item 3
Unordered list
- Item A
- Item B
- Item C
Bold text
Emphasis
Superscript
Subscript