Global Pharma Leader Enhances Threat Prioritization and Risk Visibility
The customer operates across more than 70 countries and maintains a security stack that includes over 20 tools. With more than 300,000 assets and a rapidly evolving threat landscape, they needed a better way to identify, prioritize, and respond to vulnerabilities.
The Challenge
The Challenge: Threat Prioritization & Exposure Management
This customer’s teams were investing significant time and resources to manually identify and address vulnerabilities at scale. Their existing tools evaluated CVEs and control gaps, but often lacked insight into whether vulnerabilities were actually exploitable in their environment. Many of the tools in place failed to factor in compensating controls, internet exposure, or whether existing defenses could neutralize the risk. As a result, the organization faced difficulty in determining which exposures warranted immediate attention.
The Solution
Zafran stood out by aggregating vulnerability signals and applying advanced risk context, including runtime presence, internet exposure, and threat actor activity, to identify the exposures most likely to be exploited.
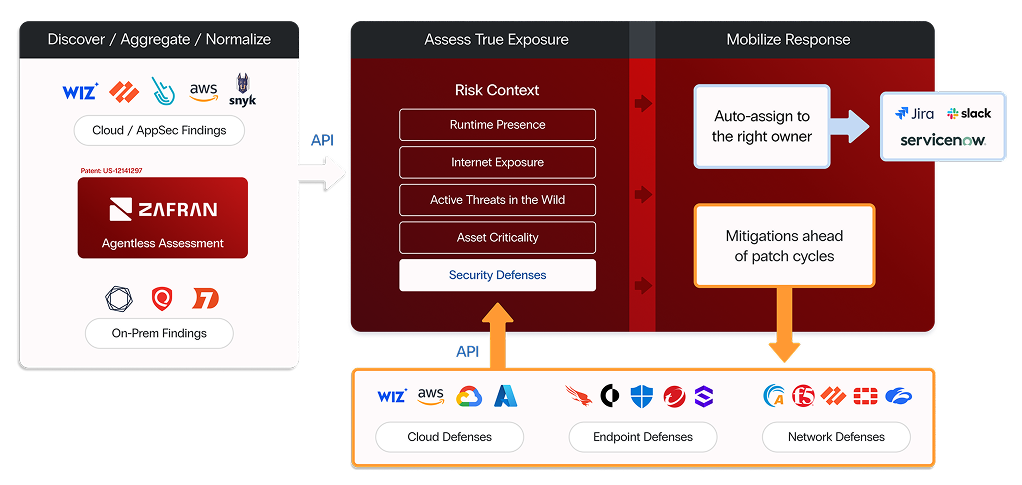
Zafran's ability to surface internet-facing assets was especially impactful. In one instance, the customer identified four exposed assets linked to activity from threat actor group BlackBasta—two of which were internet-facing and two that had misconfigured security controls.
Zafran also enabled the customer to evaluate the effectiveness of their existing security stack, turning previously passive defenses into active inputs for risk prioritization and decision-making.
Implementation
Implementation was performed in-house with support from Zafran.
Results
With Zafran, the customer transformed how they manage cyber risk and streamlined remediation workflows by consolidating overlapping vulnerabilities and surfacing only the most actionable items. This drastically reduced ticket noise and optimized the use of both internal and outsourced resources.
Zafran identified the riskiest 0.004% of assets exposed to the internet, and found they lacked active firewall protection. This level of visibility, delivered in under 5 minutes, helped the customer take immediate action to harden their perimeter.
Overall, they achieved a 95% reduction in critical CVEs, enabling security teams to shift focus from blanket patching to precision mitigation. Today, Zafran is a cornerstone of the customer’s exposure management strategy, continuously evaluating defenses against known threat actors and supporting M&A due diligence with scalable, risk-based visibility.

They are a Fortune 500 pharmaceutical company operating in over 70 countries worldwide.
Industry
Primary Use Cases
Key Outcome

25K+
In under 5 minutes, Zafran uncovered over 25K vulnerabilities across 10 assets thought to be protected by firewalls
See Zafran in action
Learn More
Zafran partners with complex global organizations to help them move from reactive vulnerability patching to proactive risk reduction. With Zafran, security teams can focus on exposures that actually matter—based on live context from their own environment—and take immediate steps to mitigate risk.
We invite you to see what our customers already know. Come see the power of Zafran.
See Zafran in Action
Prioritize and fix what is truly exploitable using risk context from your existing security tools



